A great deal has been said and written about BYOD (Bring Your Own Device) programs and their real-world impact on today’s businesses, employees and IT departments. Regardless of your feelings on that matter, there’s no doubt that BYOD has and will continue to influence the conversation around how IT departments need to adapt to the changing world around them.
For most companies, BYOD is seen as a positive move forward. But it does have challenges. Last year, my firm, TECHnalysis Research, fielded a survey with over 300 US-based IT professionals split evenly across small, medium and large businesses. One particularly interesting data point from this BYOD report is that 20% of overall respondents and nearly 30% of mid-sized companies said that, while they dove into BYOD headfirst early on, they’ve started to pull back a bit recently. A key driver for those pullbacks, in many situations, is bound to be security-related issues.
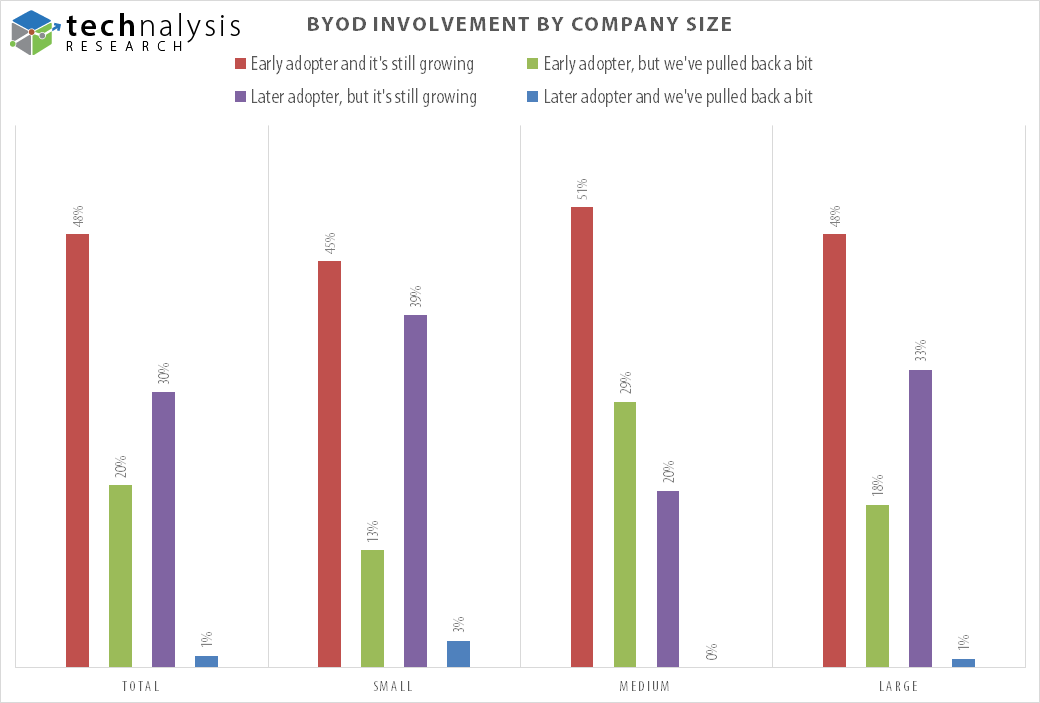
©2014, TECHnalysis Research
Virtually every week we hear and read stories about critical corporate data being compromised because an individual employee’s device was lost or stolen. Given these security concerns, it’s probably not surprising to hear that, according to that same survey, 43% of all companies with BYOD programs have a policy to wipe corporate data from a lost or stolen device. But what is surprising is that a larger 46% of that group wipe out all data on the impacted device—both corporate and personal. Given the increasingly important role that personal mobile devices play in people’s lives—they’ve become the primary camera and digital photo storage device among many other things—completely wiping all that data is clearly an unacceptable solution. Plus, only 26% of employees thought their company wiped all data on a lost device, demonstrating a huge (and potentially litigiously dangerous) gap in understanding between the two groups.[pullquote]Nearly 30% of mid-sized companies said that, while they dove into BYOD headfirst early on, they’ve started to pull back a bit recently.”[/pullquote]
In order to address these concerns, IT clearly needs to develop policies that honor the company’s right to safeguard its own data, while at the same time respecting the individual employee’s desire to not lose their precious data. (Plus, if we’ve learned anything from BYOD, it’s that IT needs to develop win/win solutions for both themselves and employees, otherwise employees will find ways around whatever perceived restrictions IT puts into place.)
One key answer to these challenges is the use of containers, which can separate personal data from work data. Solutions that enable containers allow IT to continue managing access to corporate data and applications, while leaving personal data intact. Not all container solutions are created equally, however.
IT managers need to consider all aspects of a container solution as they do evaluations. How does it work with user authentication and identity? What mobile and desktop platforms does it support? Is it a complete solution or only a partial one that needs to be cobbled together with several other products from several other vendors?
By deploying a robust container solution, IT can feel free to impose very strict, very secure policies around corporate data, while still giving employees access to their own data. In doing so, they can enable all the potential benefits of BYOD, without falling prey to its potential pitfalls.

The whole idea of BYOD seems weird to me, at least the part where a device gets shared personal and professional use: I’m unaware of any solution in which the company has a) has enough control to guarantee their data’s security and b) I can be certain the privacy of the “personal” part of my device won’t (can’t) be infringed. The only case I can imagine where I’d be OK with a company having admin rights on my personal PC/Phone/Tablet would be inside a VM, and that wouldn’t/shoudln’t be enough for them (viruses and keyloggers on the host OS…).
I’m not quite being paranoid: I have personal examples of offices taped by management, personal mail being read by IT and management…
If I have to, I’ll be happy to buy a new device or two, dedicated to a new job. Unless they’re happy with a VM, it will be a dedicated device though, and my personal stuff will stay in its own separate phablet.
In principle I agree, though in practice the idea of managing two devices is too hard. If my company were to lockdown the device any more than requiring a long password though I’d probably get a second device (and not carry it after hours). By the way, I’d point out that TouchID has really helped in this area, because the complex passwords required by most companies don’t interfere nearly as much when you use your fingerprint.
db
I wonder if this is part of IBM’s play too – they are very early adopters of BYOD (and famously locked Siri out). I wonder if they realize companies will need to standardize, but unlike with PC’s where cost was the key factor, “these days” experience and security matter more making it possible that in a couple of years we’ll see iOS be a defacto enterprise standard.
db