In December 2015, Syed Rizwan Farook and his wife, Tashfeen Malik, went on a shooting rampage at Farook’s San Bernardino workplace. The FBI wants access to data stored on Farook’s work-issued iPhone 5c. Farook’s iPhone is password protected. The FBI convinced a court to issue a writ, under the All Writs Act, compelling Apple to create a new operating system that could be downloaded to the phone in order to remove certain protections so that the FBI might “brute force” its way into the locked iPhone by rapidly entering numbers until the correct passcode was discovered.
The case is barely three weeks old, yet already, there have been a flood of legal pleadings, amicus curiae (friend of the court) briefs, letters to the court, not to mention numerous impassioned press releases. Further, there is a 50 page order from a court in New York denying the FBI’s claims against Apple in a legally similar, yet factually distinguishable, case.
I have read every word of the above so you don’t have to. You’re welcome.
The issues involved in this case are numerous and complex.
(The) case is like a crazy-hard law school exam hypothetical in which a professor gives students an unanswerable problem just to see how they do. ~ Orin Kerr, professor at George Washington University Law School
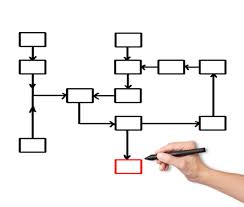
So very many words have been written already, and so very many issues have been raised in regard to this matter, that I thought it might be helpful to create a “flow chart” that would provide some structure and help us to understand the order in which these many issues are going to be considered and resolved. So let’s get started.
This matter can roughly be divided into five stages:
— Things that look interesting, but that don’t really matter
— Legal
— Legislative (Policy)
— Constitutional
— Technological
Let’s take a brief look at how each stage matters and how the stages will flow, one into the other.
Stage 1: Things That Don’t Really Matter
FLOWCHART: Skip stage 1, proceed directly to stage 2.
There are many, many speculative issues swirling in, out and around this case that are utterly fascinating to talk about…but which, in the long run, won’t matter a hoot. Some examples are:
— There’s nothing of interest on the phone and the FBI knows it. Doesn’t matter.
— The FBI could have gained access to the contents of the phone through a variety of methods that didn’t require Apple’s assistance. Doesn’t matter.
— The FBI was either incompetent or they deliberately changed the iCloud user name on the Phone so that iCloud backups could not be used, thus forcing the current legal case. Doesn’t matter.
— The All Writs Act is old. Doesn’t’ matter. (The Constitution is even older and we still consider it to be relevant.)
— The government could not get what they wanted from the legislature, so they are trying to use the All Writs Act as a vehicle for allowing the courts to grant them the power that the legislature denied them. Doesn’t matter.
I’m sure that I have missed a dozen more interesting, but ultimately unhelpful, issues.
Instead of focusing on what doesn’t matter, it’s best to focus our attention on those issues that matter and matter most.
Stage 2: Legal
All sorts of miscellaneous legal issues have been discussed in the press, but it all comes down to this:
Can the Courts order the relief the FBI is requesting using only the authority conferred under the All Writs Act?
UNDERSTANDING THE ALL WRITS ACT (AWA)
To answer that question, the first thing we need to understand is what the All Writs Act is, what it does and what it doesn’t do. Briefly, the All Writs Act was an act passed by the first congress, after the passing of the constitution, but before even the adoption of first ten amendments, now known collectively as the Bill of Rights. So it’s old, yes, but it also keeps venerable company. (((T)he AWA was enacted the same week that Congress proposed the Fourth Amendment. The Judiciary Act of 1789, which included the AWA, was signed into law by George Washington on Sept. 24, 1789. The next day, on Sept. 25, Congress passed a joint resolution proposing the Bill of Rights that included the Fourth Amendment. In my experience, those who say the AWA is too old to be relevant also tend to believe that the Fourth Amendment should be interpreted expansively in our technological age. But it’s not obvious why one ages like a fine wine while the other ages more like milk. ~ Orin Kerr, professor at George Washington University Law School))
The All Writs Act is designed to allow the courts to use the power they already possess in order to fill in any procedural gaps necessary to implement existing law. The FBI argues that the All Writs Act gives the courts — as it has many, many times before — the power to compel a third-party to assist law enforcement. Apple argues that what the court is demanding — the creation of new software — is not a case of the courts filling in a “gap” between existing legislation, but rather a case of the courts granting themselves a wholly new power authorized neither by the legislature or the constitution.
UNDERSTANDING CALEA
CALEA is the acronym used to describe the Communications Assistance for Law Enforcement Act. CALEA matters to us for five reasons. First, where the legislature has spoken, the All Writs Act does not apply.
Where a statute specifically addresses the particular issue at hand, it is that authority, and not the All Writs Act, that is controlling. ~ The U.S. Supreme Court, Pennsylvania Bureau of Correction v. U.S. Marshals Service, 474 U.S. 34, 43 (1985)
Second, CALEA directly addresses the question of encryption. Third, CALEA covers certain telecommunications companies but it specifically excludes companies like Apple. Fourth, the FBI tried, and failed, to extend CALEA to cover companies like Apple and to broaden the scope of the FBI’s control over the encryption made by those companies. Fifth, and finally, under CALEA the government cannot prohibit a company from using encryption, nor can they tell a company how their encryption must be designed.
Apple argues that CALEA is comprehensive and that there are no “gaps” for the All Writs Act to fill. The government argues that CALEA is old, out of date, ((It’s a little ironic that the FBI thinks the 227 year old All Writs Act is perfectly applicable to this matter, but the 22 year old CALEA is not applicable because it’s old and out of date.)) a hodgepodge of rules that do not comprehensively cover the issues at hand, and that the All Writs Act was created to create remedies, like the one currently being requested by the FBI, when no other remedy was available.
UNDERSTANDING “BURDENSOME”
Even if CALEA, does not preclude the Courts from Applying The All Writs Act, the FBI still has to show — based upon case law interpreting the proper and appropriate usages for the All Writs Act — that their requests would not be “unreasonably burdensome.” ((United States v. New York Telephone.))
The government argues that Apple is a company valued at well over 200 billion dollars, and that it can easily spare the services of the 6 to 10 engineers for the 4 to 6 weeks that Apple has estimated the demanded task will require.
Apple argues that the short-term costs in terms of reputation, brand, customer loyalty and bottom line profits are far more extensive than the mere cost of losing some of their finest engineering talent for a finite period of time.
Further, Apple argues that the long-term damages are far more costly, and the consequences far more severe, than the FBI is willing to acknowledge. Apple would be creating software that was antithetical to their business purposes; software that hurts their customers by weakening security; software that would turn a part of Apple into a permanent FBI forensic laboratory. Further still, similar demands from the FBI, other government agencies and, eventually other foreign powers, would be virtually endless. Perhaps most importantly, allowing the All Writs Act to be interpreted in the manner desired by the FBI would allow the FBI to endlessly broaden the scope of its demands upon Apple, and others, in the future.
Apple’s last set of claims are all future oriented and only valid if this case does not just involve one phone, one time, in one case, but is a precedent that will be made applicable to all phone makers, and all phones made, going forward. This is why both Apple and the FBI are fighting so bitterly over the question of whether this case is about merely one phone or whether it is about setting a lasting legal precedent.
FLOWCHART: Go to stage 3
Stage 3: Legislative
I want to make one thing very, very clear. When I’m talking about the FBI not being granted the kind of investigative powers that they’re demanding, I’m talking about being unable to get them from the COURTS using the ALL WRITS ACT. That does not, in any way, preclude the FBI from getting what they want by obtaining a new LAW from the LEGISLATIVE Branch. What the Courts can’t or won’t grant to the FBI, the legislature can and may. After the courts have made their decision — and even before the courts have made their decision — the FBI can turn to the Legislature for relief. In fact, the legislative battle is well begun.
— Press releases designed to sway public opinion are issued on a weekly, and sometimes on a daily, basis.
— The Senate has already started congressional hearings on the matter.
— The French legislature has already voted on legislation that affects this matter and which may dramatically and unalterably change the terms of the debate.
FLOWCHART: Go To stage 4
Stage 4: Constitutional
Once Congress has crafted new legislation — and that may occur within months or it may take years — it will have to undergo Constitutional scrutiny. Since the legislation has not even been drafted yet, it is impossible to know what Constitutional challenges such legislation may face or how it will fare in overcoming those constitutional challenges. We can be confident that there will be First Amendment (compelled speech), Fifth Amendment, and perhaps even Thirteenth Amendment (involuntary conscription) issues, but everything else is speculative at this time.
FLOWCHART: Game not over. Go to stage 5
Stage 5: Technological
Stage 5 is the conditional “if-then” statement of our flow chart.
I believe that it is a certainty that Apple is closing the technological loophole (system updates without the phone owner’s knowledge or permission) that the government is attempting to use in the San Bernardino case. It’s only a matter of “when” not “if”. And when it happens, access to future iPhones will be beyond the reach of the All Writs Act and the FBI’s only recourse will be to obtain legislation demanding that Apple not make unbreakable encryption and instead always create a vulnerability in their encryption specifically designed to allow the FBI easy access to the contents of any iPhone, upon demand.
In other words, technology is going to clear the table and reset the game. Almost everything that has gone on before will become moot. ((Lawyers do so love to use the word “moot” and we so seldom get the opportunity to use it in its proper context.))
FLOWCHART: If (when) encryption improves, then go to stage 1.
Conclusion
The parties to this case are in it for the long run. It’s going to be a marathon, not a sprint.
Tomorrow, I will focus strictly on the legal aspects of the current cases and project who the winner may be.
Author’s Note: This article is part 1 of 2. Part 2 was going to dive into the Legal issues involved in this case since the legal issues are the ones that will most likely be decided first and foremost. I had intended to publish part 1 on Saturday and part 2 on Sunday. However, the FBI issued a 30 plus page reply to Apple late on Thursday afternoon and much of the material in the FBI’s pleading covers the very same legal questions that I was addressing in my article. I decided that it wouldn’t make sense to publish an article that didn’t integrate these pleadings into the discussion, so I am delaying my second article until I have had time to do that. When it’s done, the article will focus on:
1) Defining the scope and limitation of the All Writs Act;
2) Whether CALEA precludes the use of the All Writs Act; and
3) Whether the FBI’s request is “burdensome” as defined by the case law defining the All Writs Act.
In addition, I fear that I must also specifically address the question of whether this case is focused on just one phone or whether it is precedent setting. Normally, I would reserve examination of this question for the Constitutional issues, but it is directly relevant to the question of whether or not the FBI’s request is burdensome under the terms of the All Writs Act.
Author’s Query: I am most definitely going to write the second article in this series, but I would like to know whether you want to hear more about FBI v. Apple, or whether you are suffering from legal overload and would prefer that I return my attention to more business centric issues. Let me (gently) know in the comments, below.
Thanks for this. While I’m no expert I’ve noticed that much of the discussion around this issue seems to fall into the “does matter matter” category as you’ve described. This case is not simple enough for laymen such as myself to predict because the outcome will likely come down to analysis of a large volume of case law. I’ll keep this URL handy to point to as evidence of this fact.
Thank you for your feedback.
Not only can’t laymen figure this out, experienced lawyers can’t either. I’ll repeat what professor Kerr said:
“(The) case is like a crazy-hard law school exam hypothetical in which a professor gives students an unanswerable problem just to see how they do.”
I am currently working on one article, which I may have to split into three articles ,on some of the most pressing issues in this case.
1) Does the CALEA legislation make it inappropriate for the courts to decide this issue under the authority of the All Writs Act?
2) Is this case about 1 phone or will it set a legal precedent? The answer to this question is crucial because it dramatically affects the next question.
3) Is the court’s order “burdensome”. The All Writs Act has limitations. I’ll go into those limitations in great detail in my article. If this case involves a precedent, then the burdens on Apple and others are enormous and ongoing. If this is just about one phone, then Apple’s “burden” in this matter is far more limited.
In my view, if Apple were ordered to carry out the FBI’s wishes it would absolutely set a dangerous precedent. Therefore I feel Apple will not be forced to.
I think there are 2 distinct questions, tied up nicely in “does the end justify the means ?”
A) The end is for the FBI to have access to a phone’s data when they have
1- a warrant
2- physical control of the phone
3- legal possession of the phone
I’m OK with that. Actually, I support that.
This is not warrantless mass spying. This is not a remote hack. And this not new: all phones up to 2 years old can be hacked, as can all current active and/or TouchID phones. This is not overwhelmingly new: the FBI already have access to the phone’s last cloud backup, they want to scrape the extra info that’s new since the last backup, or not backed up,at all.
B) The means, since there is no law directly pertinent to that case and officially no technical way at the FBI to break into a locked + password-protected + password-changed phone (they have no issue achieving their goal if any of these 3 conditions isn’t met), is the AWA which is very open-ended and in its broadest can be understood to empower judges to have individuals and corps do whatever they want.
That’s an issue, because once Apple get forced into writing that code and setting up that lab, they maybe could be slippery sloped into the “warrantless” and “remote” cases.
That’ a big issue and makes using the AWA very undesirable. There should be a specific law that defines both law enforcement’s powers and limitations, and makes sure that every IT provider doesn’t turn into one of Big Brother’s eyes everywhere, all the time, for anyone that’s a LOVINT.
The issue was bound to pop up. It’s good it’s being discussed, hopefully it will even be legislated in a sane way.
Wholeheartedly agree! Very well put.
“and others”
Which is a very real possibility for the tech sector overall, and not just device makers.
Joe
“since there is no law directly pertinent to that case”
Well, Apple says CALEA is directly pertinent. The FBI says CALEA has gaps that the All Writs Act can fill. But what the FBI is asking from the All Writs Act is not “filling gaps” in CALEA. It’s asking the court for a remedy that would NEGATE CALEA.
“This is not a huge new backdoor”
Welllllllll, yeah, it kind of is. The FBI is asking Apple to create a specialized one-time operating system, designed to work on one single phone. No one has ever been asked (or compelled) to do that before.
Indeed, but that’s because it never was necessary before. That’s why I say the backdoor isn’t new: it used to be there, it has been removed, the FBI wants it back.
Fire exit, concrete truck.
Technically it wasn’t a back door so much as something that wasn’t as strong as it could be getting some re-inforcement.
What’s interesting is, when you cast it as a case of Apple being uncooperative, and everyone else doing their civic duty (since others haven’t been called out in the same way).
One wonders though, if it can’t be cast another way: Apple really is concerned with user privacy; and others either aren’t so concerned, or they have a system that makes it extremely unlikely they can ever adequately redress security concerns without practically starting from scratch.
Context matters. When there was a backdoor, everyone knew about it, so people, including companies, were more prudent about what personal and financial data is put in a phone. With the deployment of strong encryption, the industry felt far more comfortable about security and the range of transactions that we can conduct using the smartphone expanded. So reestablishing a backdoor now is not is not a mere return to the old backdoor regime. The landscape has changed. A lot more stuff that can be stolen and eavesdropped is in our phones. Put in a backdoor today and you trigger a massive retrenchment in smartphone functionality. Do we really want the industry to go backwards?
There are still backdoors and leaks everywhere: any unlocked phone, any phone locked w/ biometrics instead of password, any locked phone with a relevant hack, most (all ?) servers and cloud providers have been hacked by now, most apps are unsafe including OSes and browsers… Thinking that because one part of the chain is presumably safe some of the time, safety has been attained is a dangerous delusion.
If we could rely on technology to enforce laws, car thefts and burglaries would be a thing of the past. Ditto in IT. Tech isn’t a substitute for law enforcement. The reason I’m not a daily victim of crime is because the overwhelming majority of people aren’t criminals, and the very few that are get caught. Not because I can fight/shoot, my home is burglar-proof, my car unstealable.
re. IT crime, there is a scale issue (one burglar can only burglarize so much, one hacker isn’t physically limited) and a territoriality issue (the burglar has to be there, the hacker, not). Laws have to adapt to new tech, too.
“There are still backdoors and leaks everywhere”
And yet, here we are, wondering why the FBI needs Apple’s help to even make it feasible to brute force the phone in its possession.
“Thinking that because one part of the chain is presumably safe some of the time, safety has been attained is a dangerous delusion.”
Yes, generally, having a lock on the door of your house does no good, unless you actually lock it.
“There are still backdoors and leaks everywhere…”
Then why the debate and need for help?
Surprised we still have to clarify that:
1- the FBI says they want data after the last cloud backup and the phone is locked and data that may be local-only. Most data by far is backed-up regularly, duplicated in the cloud, and phones aren’t locked. 99.999% of the cases are way simpler to hack than this one.
2- Because the FBI want to set a precedent
I believe there hasn’t been any wants of precedent. Just a desirable or undesirable outcome.
If the statement is “there are still backdoors and leaks everywhere…” the need for assistance is not necessary. Fine if the FBI wants the data, that’s not contested, it’s the method and process that is argued.
These are the most notable data breaches of 2015 in the US: http://www.networkworld.com/article/3011103/security/biggest-data-breaches-of-2015.html . They total about 150 million, some went on for about a year.
What’s one more device ? An extra hole in a million-holes sieve ?
Why is that specific instance of the rightful owner of a device, backed up with a warrant, getting so much more attention than the 150 other, unwilling, unlawful, million ?
Would the conversation be different if the device did not have an Apple logo ?
Or more muted ? Nothing much was made of RIM’s case: http://www.developingtelecoms.com/business/vendor-news/6169-blackberry-exiting-pakistan-following-privacy-dispute.html
“Why is that specific instance of the rightful owner of a device, backed up with a warrant, getting so much more attention than the 150 other, unwilling, unlawful, million ?”
It’s the right case to escalate. The right type of ‘perp’. The right timing. The right state of mind of citizens. The right timing of political interest.
But, intentions? No. Just a hope for the right outcome for the FBI. The government exhibited patience for the ducks to line up. Parade the ducks around and let shots be fired, hopefully they all fall in place and future problems solved.
Calculated? Yes.
Career ending? Sure, if if goes wrong.
Career Ending? Sure, if all goes right in the now, but later blows up.
Either way, it’s potential career suicide.
“Would the conversation be different if the device did not have an Apple logo ?”
Probably not, but no other conversation is happening. Presumably, the FBI is not looking for help with any other devices.
You missed Longboard’s point: “Why the debate and need for help (‘conversation’)” …. if “There are still backdoors and leaks everywhere” (including on iPhones)?
Sounds like, when the built-in security measures on the iPhone are actually enabled (encryption with a password), there are no backdoors or leaks. Hence the “conversation”, with the FBI seeking help.
Again, it goes without saying: a door with a lock that isn’t locked isn’t much of a deterrent. But, if you want to call that state of remaining unlocked a “backdoor or a leak” on the order of a locked door that does not require assistance to enter, then by all means knock yourself out. No wonder you are confused by the conversation.
I didn’t miss his point, you missed my answer and the background info:
– aside from iPhones, the top few hacks last year in the US affected 150 million people, and these were not “hacks” by the owner of the device, with a warrant. It seems to me to be a much more pressing issue.
– for the iPhone, any “live” iPhone can be hacked (iOS is the OS with the most vulnerabilities) , any iPhone “secured” by TouchID can be unlocked w/ a lifted fingerpint (that doesn’t require consent), and any iPhone data backed up on Apple’s cloud (even password-protected) can be subpoenaed and decrypted. (Apple has the backup’s password and will relinquish it, to US authorities and presumably others.
You’re the one not even understanding the basic setting of the issue.
Not at all. I’m well aware of exactly what you are saying.
My iPhone is physically vulnerable in someone’s possession if I have not used the passphrase lock and rely on fingerprint alone. Just as someone can mug me at my door and take the key to my house.
Furthermore, data I store anywhere that is not local and under my direct supervision is also vulnerable (unless I further encrypt it before uploading it).
Lastly, Apple does in fact cooperate lawfully where and when it can, despite the smearing it is getting.
What Apple is not prepared to do, and has seemingly never done, to the admiration of its users, is to unlock a user’s locked phone, wherein the user can expect to have private data locally that is (uniquely?) not vulnerable to hacking or handing over (obviously, or there would be no need to help the FBI).
You continually seem to miss, misunderstand, or dismiss that last point in your incessant sentiments to the effect, “well, what’s one more phone, nothing’s safe anyway”, “who cares, someone can grab your fingerprint anyway”, “what’s the big deal, no one cares about privacy anyway”… Certainly, all these sentiments would be true — if Apple didn’t hold its ground.
You’re wrong, again: Apple was unlocking phones before the 5 or 5s, actually their phones could/can be unlocked by anyone. So “However, what Apple is not prepared to do, and has seemingly never done, to the admiration of its users, is to unlock a user’s locked phone,” is wrong, and (suprise !) your admiration is misplaced.
What’s so not-special about giving up the backup with its password, but so special about giving up the device’s lock ? If the question is that important to people, why didn’t they sit up when RIM exited Pakistan, or Google exited China (countries where “admirable” Apple is happily doing business), or 150 million people got hacked last year in the US alone ?
Apple isn’t holding any ground, they don’t have any ground to hold. They hand over backups and keys when asked, do business w/ China, have the 2 worst OSes security-wise… (new today: any app can be local-installed on any iPhone via transplanted security certificates: http://thehackernews.com/2016/01/ios-apps-jspatch-hack.html ).
http://uk.businessinsider.com/apple-never-unlocked-iphone-for-law-enforcement-2016-2?op=1?r=US&IR=T
http://images.apple.com/privacy/docs/legal-process-guidelines-us.pdf
from your first link: “The company does say, however,
that in the past, “and under a lawful court order,” it has “extracted
data from an iPhone” that used operating systems that came before iOS 8, which was released in 2014.”
Extracting data didn’t required unlocking before, and Apple did it. The only reason for the unlock is to get at the data.
The FBI is now not even asking for the data, not even asking the unlock, but only for tha ability of an infinite number of tries at unlocking. That’s way less than Apple used to do, and still does for anything below iOS 8.
Obviously you aren’t reading John Kirk’s article and all the comments with any comprehension.
It isn’t “way less” when the means don’t currently exist.
It isn’t “way less” when everyone may now line up because they say there is some “contagion” on the phone and a precedent has been set where at the moment it is not possible.
That’s right, the FBI is not asking for the data, because that avenue currently is not open to them. It’s impossible. And Apple is contesting any call for them to even attempt it. (Yes, that is holding ground in any sense of the term).
Apple is closing any vulnerability it can find. So that there are not the “backdoors and leaks” everywhere that you proclaim. Of course, to you, all this means the exact opposite of Apple being concerned about user privacy.
Hence my “might makes right” question. Getting data off a phone used to be possible. No Apple have either closed it or made it very costly. I’m not OK with a private company deciding what law enforcement can or can’t do because they’ve got the tech/brute force/weapons/money/influence to back it up.
Apple like all others is running around trying to plug leaks, and springing new ones constantly (see my link about today’s new exploit). Making a big fuss about the least contagious, most controlled of those leaks is very hypocritical. Plus undercutting their own ‘we’ll never break them !” locks by allowing biometric bypass, on top of being the least secure OS around is actually funny.
You are fussing and hypocritical. If there are real leaks and vulnerabilities, the FBI wouldn’t need Apple’s help.
Obviously you aren’t OK with Apple “deciding what law enforcement can’t do”, that’s your choice. Personally, I’d rather the govt deal properly with guns. Really, it’s “fetishising the phone” for law enforcement to think they can’t solve or prevent crimes without being able to do what they want and possibly obtain evidence they never had in the past.
Others are glad Apple is doing this. Apple has the money and tech to do this, because they have made choices that make that possible. The choices are aligned to a lot of user’s interests. Google uses its money and might to do what is not in my interest.
As far as what is “right”: until the debate is concluded and democratic/referendum-driven legislation says otherwise, I will go with Ben Franklin’s “Those who give up their liberty for more security neither deserve liberty nor security,” before going with a fickle govt that forgot that only last year it called for China not to do what it is now doing.
“and possibly obtain evidence they never had in the past.” Wrong, that’s the contrary: evidence they *always* had in the past.
Being grandiloquent vs FBI is fine. What would be finer is being efficient vs the hundreds of millions of hacks that are done 1- remotely 2- not by the owner 3- w/o a warrant 4- for nefarious purposes.
I think the tech kommentariat is utterly picking the wrong battle to get all excited about, and because Apple’s in it. Nobody’s taking Apple to task for the below chart, which is much much worse:
source http://www.gfi.com/blog/most-vulnerable-operating-systems-and-applications-in-2014/
When I say in the past, I mean before 2007 or the invention of smartphones.
And when evidence from other phones, tapped for the better part of 100 years, is sought/recorded/analysed, the content may or may not be encrypted, garbled, and or spoken in a code known only to the parties speaking.
So, in that way, I say usable evidence is “possibly” obtainable: it’s possible, as always, that “evidence” obtained is unusable; it’s never a done deal. Law enforcement, as always, has to deal with that. Usable evidence is not their *right*, they have to work for it.
OH MY GOD!!! THERE ARE UNEXPLOITED VULNERABILITIES IN APPLE PRODUCTS!!!!!!!!!!!!!!!!
unexploited ?
http://www.iphonehacks.com/2015/09/apps-infected-by-xcodeghost.html
http://www.techworm.net/2016/03/acedeceiver-malware-attacks-iphones-via-apple-drm.html
the list goes on… shouting doesn’t make it go away, sorry.
As John Kirk outlined in the article, it seems that it is CALEA that already says specifically “what law enforcement can or can’t do”. It’s the specific law trumping the more general one that the FBI prefers.
It seems it was a hard-fought deal. And now the FBI doesn’t like it. Here is an article describing the situation simply:
“https://backchannel.com/the-law-is-clear-the-fbi-cannot-make-apple-rewrite-its-os-9ae60c3bbc7b#.su2c6tftj”
“the FBI already have access to the phone’s last cloud backup, they want to scrape the extra info that’s new since the last backup, or not backed up at all.”
Except, again, the FBI gets what they get with the iCloud backup. If the back up is encrypted, it’s encrypted. And apparently you need the phone unlocked to un-encrypt it.
You seem to act like Apple is playing two sides, and only paying lip-service to privacy for PR reasons. They are simply cooperating with law enforcement as far as they can, and at the same time they do provide the possibility for a user’s data to remain private.
Wrong: Apple have the backup encryption keys, device unlock is not required to decrypt backups: http://9to5mac.com/2016/02/25/apple-working-on-stronger-icloud-backup-encryption-and-iphone-security-to-counter-fbi-unlock-requests/
My understanding, is that, at least for later iPhones, hardware encryption is happening on the phone, not after the backup reaches the server. And that one of the keys for that encryption is provided by the device and not known to Apple.
The article is from last month, that probably hasn’t change since then.
In order to provide users the flexibility of moving backups from one device to another (say in the event of a new phone or iDevice), the iCloud backup cannot use any one specific device’s hardware key.
iCloud backups are encrypted in transit, and they are stored using Apple’s encryption key and released with proper login credentials.
Possibly? The events and rhetoric, which are becoming increasingly fearless and contemptible, point to their real goal, that is total power, where non compliance is criminal by definition. The so called terrorism case, barely different from the rantings of any of your mass murderers, is the volatile, easy to point at hook to distract the masses from the real purpose of this new push to overrule the pesky courts.
Why do you think there there is an endless supply of television and movies depicting selfless and brilliant police/security work saving us from evil? Because it’s true?
Please do write part 2.
“The government argues that Apple is a company valued at well over 200
billion dollars, and that it can easily spare the services of the 6 to
10 engineers for the 4 to 6 weeks that Apple has estimated the demanded
task will require.”
I am a legal ignoramus, but isn’t it so that “burdensome,” as defined by courts, normally has little do do with cost or affordability?
Normally, what the court is doing is, for example, asking a store owner to provide the police with his security footage. Not much of a burden.
Here, Apple has estimated it’s initial costs as 6 to 10 engineers working 4 to 6 weeks.
However, the list of burdens grows very, very long if this case is indeed about more than one phone. My article will go into this in great detail. Just a couple of the issues involved:
— Apple is not being asked to produce something that exists, they’re being asked to create something that doesn’t exist. So far as I know, this has never been authorized before under the All Writs Act.
— Apple is being asked to take an action that is antithetical to their business. They’re being asked to set up a separate division within their company to hack their users and to weaken the encryption being created by another part of the company. Burdensome? Oh yeah.
— There are tremendous policy issues here too. But none of them come into play UNLESS this case involves more than 1 phone.
I’m working on the article as we speak. It’s going to be LOOOOOOONG and detailed. But hopefully, it will be enlightening as well.
@FalKirk:disqus I am looking forward to your LOOOOOONG and detailed article as I am sure it will be interesting, enlightening and informative.
Thanks, Brian…
…but be careful what you wish for. 🙂
I would be okay if, like eminent domain, Apple were reimbursed by the government for time/effort/expertise. Of course, it’s not what I think, but rather what the law says.
“Apple is being asked to take an action that is antithetical to their business.”
Well boo hoo. This whole new OS overstated nonsense is nothing more than a firmware patch, something only Apple is uniquely capable of providing. Even a non lawyer like me can tell you that these are all under FCC license. Licenses have terms, they are not rights.
“Well boo hoo. This whole new OS overstated nonsense is nothing more than a firmware patch.”
Klahnanas, I knew you’d blow this off as being non-burdensome. You didn’t disappoint.
Hmm. I suspect I will be devoting between 1,500 hundred to 2,000 words to this exact question. We’ll talk then about whether the FBI’s request is going to be burdensome or not.
Your anticipation of my reaction was correct, perhaps for the wrong reasons. I’ve been careful not to make this an “Apple” issue. It really isn’t, and I’ve stayed away from opining on what Apple’s motives may be.
Where you might be wrong in your anticipation would be my motives. I would have said the exact same thing, over the same BS, regardless of which company. I did agree that it can become too burdensome, and that such help should be reimbursed as well.
What kind of reimbursement would suffice for ordering a company to undo or negate its:
overall product strategy and roadmap
carefully considered hiring decisions
countless man-hours of hardware design and software coding
security white papers
million+ dollar marketing campaigns
customer goodwill
brand identity
You think this comes down to simple reimbursement?
If they are going to call the removal or isolation of a counter “a whole new operating system”, they are technically correct. Considering that might involve one to ten lines of code to create this “whole new operating system” is what is BS.
Laws change, situations change, society is not bound to preserve their product strategy or roadmap. That is very much Apple’s problem.
Society has a much larger problem, that is how to properly maintain the 4th Amendment without throwing away reasonable searches and seizures.
“Society has a much larger problem, that is how to properly maintain the 4th Amendment without throwing away reasonable searches and seizures.”
Which seems to be precisely what the FBI/DOJ are obscuring.
There is no obscuring, the intent is in the open, as are the facts of the case.
Apart from the issues of precedence and whether this is about the one phone, or not; and other items in the press campaign conducted by the govt, you mean? (And these are mentioned in just this article; other articles raise other concerns).
And your attempt to minimize the impact on Apple (and society) is BS.
This phone, and any future phone, can be seized at any time. The expectation that its contents must be readily viewable is nonsense.
Why are paper shredders and open flame not outlawed? As others have pointed out, in the old days (when people didn’t carry around repositories containing details of every bit of their lives) the FBI still managed to solve crimes.
Your argument assumes that the FBI is seeking to maintain and protect access to something they’ve never had before.
As far as I’m concerned, the demand that law enforcement automatically be granted access to contents on a phone is tantamount to repealing the RIGHT to remain silent and not self-incriminate.
Who in the world said anything about automatic? I sure didn’t.
Your paper shredder example is a very good one. Conversely I also remember a certain accounting firm getting in a lot of trouble for using them.
Warranted searches are, and should be, legal.
A warrant is like a birthday card. Available anywhere anytime. Since the hurdles to get a warrant are so very very low, access to the phone is all but automatic.
More BS. To properly get a warrant (pre-BS Patriot Act) you needed to show just cause for the search to a judge. That judge bore huge responsibility for issuing that warrant.
What do you suggest, barring all searches?
No. Far from BS. You only need to show “probable cause” for a search warrant, and only the most incompetent law enforcement official would ever fail to meet that extremely low threshold. Thus, it is all but automatic.
You ask for my suggestion: I suggest that the contents of a smartphone should be considered off limits to search warrants — like medical records, priest confessions, journalistic sources and notes, lawyer/client discussions, spousal discussions, and the contents of a diplomatic pouch.
The sheer amount of data available for easy search on a phone goes way beyond the scope of any warrant. Therefore, because the possibility for abuse is so high, no search warrants for ‘phone content’ should ever be issued.
In a sane world, this would be obvious to everyone.
Probable cause is reasonable. The search presumably is also supervised, and the findings also presumably treated with decorum. Of course, there are bad actors in law enforcement. They should be punished when they violate their trust.
If I can be cavity searched to the point where the examiner’s elbow disappears, I don’t think a smartphone is crossing the line. I’m truly puzzled by this. There are so many more intimate and extensive searches, such as PCs, I just don’t see the smartphone deserving of special treatment.
Medical records are not 100% protected, journalists have been jailed for non-disclosure of source, confessions protection is more for the priest than the sinner, spousal discussions are 5th amendment protected, diplomatic pouches are protected by treaty.
“I’m truly puzzled by this.”
I’m shocked.
I’m shocked you’re not. I think we need to re-evaluate all searches, not just phones.
By the way, Apple will undoubtably be reimbursed, at least for short term costs, like labor, space and equipment.
The subtle — and more serious — costs cannot and will not be reimbursed.
Cost of doing business. Like I said, airwaves are licensed, not a right.
“airwaves are licensed, not a right.”
So, is software, even when it is on your own phone.
And why the jump from firmware to airwaves? I am not sure of the point you are trying to make.
That the law can indeed set terms on the use of the airwaves. Which can include backdoors on devices, cooperation with authorities, etc.
oh, there is no doubt the airwaves *belong* to the govt — they’ve been monitoring them for best part of a century. And everyone knows our access to the airwaves isn’t really a right, since we have all “suffered” no access at times, or been subject to all sorts of obstacles at the best of times. It’s no more a “right” than good roads to drive on.
The question is, whether you have to make it easy for the govt to know exactly what you are saying, when you use the airwaves.
John Kirk describes the current legislation and outlines what the FBI is trying to do in order to get itself new powers. John put five points under CALEA in his article. This is just the fifth:
“Fifth, and finally, under CALEA the government cannot prohibit a company from using encryption, nor can they tell a company how their encryption must be designed.”
No sir, they belong to the citizens of the US and are administered, on their behalf, by their duly elected government or it’s designate. In this case, among other’s there’s the FCC, FTC, etc.
I do not advocate mass surveillance, nor do I make an exception for a phone. If I can be searched boarding an airplane, that’s bad enough, my phone is not logically exempt.
Maybe CALEA does clarify this particular case. There’s nothing stopping the Congress from passing laws requiring a means of access under democratically acceptable terms. This matter is so above and beyond Apple that it’s not even worth mentioning it other than as a case study.
I believe the Radio act of 1927 claims no public ownership, thus government does not own it, the people do not own it; it is like wind, sun light, rain… However, the government will help manage it.
Congress deleted a House passed ownership statement. It’s a myth that people believe airwaves belong to the people. The government has said no one owns it.
The FCC manages it due to a “back-door” slip due to regulations created. And, people didn’t throw up a fight. The thought was, “well at least someone will keep it from becoming a chaotic mess”. And, as such, the FCC became big brother and enacted morals and became the vice squad.
In any event, the people do have recourse, they can switch the dial, knob, whatever it is you like and tune out the signal.
Then how in the world do they charge for it if they don’t own it?
Because they can and you cannot… You have the right to form a dissenting organization.
Thanks. So burdensome is more nuanced than mere time/money.
Two other things:
A, France – obviously France’s new law (has it fully passed yet or is it still waiting for approval from whatever they use as an upper chamber?) is going to be a long legal slog all its own, in french courts and EU courts. And France is just the first country to pass legislation that Apple will have to fight. Remember the endless apple vs samsung battles in various courts in various countries? This will probably be even more drawn out.
B, Re the irrelevancies you list in stage 1. Not relevant in legal terms from an impartial POV, but judges are fallible human beings, so all that posturing and editorializing is at least partly for the people who will make legal decisions in the case, as well as for the public/the legislators.
Yes, Judges are fallible, but I’ll say this. Before a case can get to the Supreme Court, an awful lot of very smart people will be examining the various issues from every angle possible. I don’t always agree with the decision of the Supreme Court, but even the decisions I hate are meticulously researched and reasoned.
I’m definitely suffering from legal overload about FBI v. Apple, but only because the majority of articles already written lack the clarity and insight that you provide. I’m very much looking forward to reading more about this from you.
Wow. That is very kind of you to say.
You may well come to regret those kind words when you see the stream of articles that are about to come down the pike. 🙂
“Press releases designed to sway public opinion are issued on a weekly, and sometimes on a daily, basis.”
This is the main reason why the things you say don’t matter in a legal sense still matter otherwise. I know this was not the focus of your article, but there is some massive mischaracterizing going on. The way the FBI/DOJ present their public arguments is that it is a forgone conclusion that there is evidence on the phone to put the bad people away and that Apple has been uncooperative and have blocked the FBI in all areas with regard to the phone’s data. Neither of which has been the case.
Joe
Yes, I think the legal issues are fascinating, but ultimately, Congress may well override the court’s decision with legislation. The PR battle for the hearts and minds of the pubic and congress is probably the battle that matters most.
This sound like a Supreme Court matter, where conflicting lower courts and the politics of an election cycle cloud the issue. Part 2 is anticipated.
John, you wrote:
“The government could not get what they wanted from the legislature, so they are trying to use the All Writs Act as a vehicle for allowing the courts to grant them the power that the legislature denied them. Doesn’t matter.”
But in the New York case that also relies on the AWA, the judge explicitly used that argument to deny the governments motion. The judge wrote:
“In short, whatever else the AWA’s ‘usages and principles’ clause may be intended to accomplish, it cannot be a means for the executive branch to achieve a legislative goal that Congress has considered and rejected.”
(p. 26, 2/19/16 ruling, copy easily found on eff site under “Apple All Writs Act (NY)” section.) The analysis is very interesting. The fact that the All Writs Act was used is actually very pertinent to the case.
What I was trying to say was that the motivations of the FBI don’t matter.
What you’re pointing to is the fact that the All Writs Act cannot speak when the legislature already has. I just finished working on the “CALEA” part of my next article (articles?) and I can tell you that the FBI is pushing back on this hard. Essentially, they’re claiming that 1) CALEA is not comprehensive and it’s perfectly fine for the Court’s to fill in the gaps with appropriate remedies; and 2) CALEA doesn’t apply because CALEA “does not destroy any existing authority—or even speak to courts’ power at all.”
There is a lot to unpack in these arguments and I can’t wait to finish my article and share my thoughts and observations with you all.
First, Please do write your 2nd article.
Next, you wrote “Fifth, and finally, under CALEA the government cannot prohibit a company from using encryption, nor can they tell a company how their encryption must be designed.”
Does this portion of CALEA only restrict the Executive Branch (DoJ), or does it also restrict the Judicial Branch via the AWA route?
“Does this portion of CALEA only restrict the Executive Branch (DoJ), or does it also restrict the Judicial Branch via the AWA route?”
Good question. CALEA only applies to the executive branch. There really was no need to say, “The courts can’t order a company to decrypt it’s own code”…until now.
What’s supposed to be happening is that congress passes a law and the courts use the all writs act to supplement it if failure to act would allow the legislation to fail. What the FBI is proposing is that the courts can order this remedy (and what other remedies) even if the legislature doesn’t authorize and and, in this case even if the legislature forbade it!
A good rhetorical question to ask is, “If the courts had this power all along, why did the FBI even bother going to congress in order to obtain the CALEA legislation?”
John, I’m very glad to see your analysis of FBI v. Apple, since (1) this is a difficult case, (2) you’ve proven your dissection capability in the past, and (3) you’re a former attorney (recovering you say, but it doesn’t seem like you’ve lost your skills!).
Thank you for your encouragement, Observer. It’s much appreciated.
It’s probably true that I haven’t lost my legal skills, but that’s only because they were never very good to begin with. 🙂
Can’t see the Feds prevailing, if they do, we’re going down in something akin to extra thick sewage laden quicksand…Super great article, thanks
“Can’t see the Feds prevailing”
You know, let me say something about that. I went into my research not knowing who had the advantage. The more I researched, the more certain I became the FBI wouldn’t be able to get by the twin stumbling blocks of CALEA and “burdensome”.
Then…the more I researched, the less certain I became. There are some very subtle and nuanced issues in the case. The more I learn, the less certain I become.
“Believe those who are seeking the truth. Doubt those who find it.” ~ Andre Gide
That’s piqued my worry a bit…glad to rely on you to help with the mulling over…we’ll all be staying tuned…hopefully, somehow in the end the legal process will render a ruling that’s reasonable, sensible & fair…can’t help but think that being more exposed in an already porous world could yield much benefit…I look at it as almost all risk (should the FBI get it’s way)
Get your waders out, but a gas mask is likely to be illegal. I do hope you’re right though.
I’m an optimist…I believe that wisdom (& addressing the problem in a reasonable way) will somehow, in the end prevail…but only after necessary trials & tribulations
I was an optimist too, then Bush’s Iraqi adventure and perpetual detention without due process and extraordinary rendition and waterboarding and the Patriot Act happened and I have completely lost any confidence in the wisdom of the crowd and the people who endeavor to lead them. And now we have The Donald.
I get what you’re saying…It’s not at all implausible that the political climate could change dramatically, especially if we suffer another (God forbid) 911 scale attack & someone such as Trump gets into the Oval Office
John, you say “The FBI could have gained access to the contents of the phone through a variety of methods that didn’t require Apple’s assistance. Doesn’t matter.”
Wow. It looks to me like it matters greatly. How can the FBI order Apple to do something they can do themselves? (1) Why would the FBI issue such an order? (2) There is no need for such an order, so to me, insisting on it makes no sense at all!
This is, in my opinion, one of the great red herrings leading us astray. From an equitable point of view your can (and I have) argued that the FBI should not be able to pursue this case if: 1) they self-sabatouged the phone; 2) They can go to the NSA (or in-house) and crack the phone themselves. Apple has brought up both of these issues in pleadings.
However, I can’t see a court throwing this case out on that kind of technical detail. The courts don’t necessarily want to be forced into making sweeping constitutional pronouncements, but they also know that this is not a novelty, that this issue is going to come up again and again, and they going to resolve the legal matters in this case as best they can.
Of course, that’s just my opinion.
Can FBI and/or court toss aside established law due to their dislikeness? Any precedent?
My glib answer is “no”, but I’m not sure that I am following your question. Can you clarify or elaborate?
You mentioned “The government argues that CALEA is old, out of date,” so FBI invoked AWA. I am asking is there any court precedent that laws of land are selectively used and succeeded?
Well, the laws aren’t selectively used. But the department of justice, in its most recent brief, pointed to a couple of instances where the courts have found that there wasn’t a compressive legislative scheme that prohibited the courts from using the All Writs Act. The department of justice argues that this should hold for CALEA as well.
First, thank you for “[reading] every word of the above so [ I ] don’t have to.” Seriously.
Please do continue with the Apple/FBI analysis. It’s very refreshing to see you cut through all the crap. Best,
—
kobi
Thank you for your encouragement, Kobi.
I am not kidding when I tell you that my eyes are blood-shot (and I don’t drink). Last night I read all the major cases that the FBI cited in their brief and then I went back and read some of the dissents in some of the frequently mentioned cases. The dissents in The New York Telephone Case along with the dissent in Mountain States, were particularly interesting.
Was it work? You bet. Would I have done it if I didn’t love doing it. No way.
I bet your eyes are bloodshot because of the gathering nightmare of dark forces. Thanks for keeping it together to help those with less patience and insight understand the brewing shitstorm.
I heard an interesting report on NPR talking about how this is easily accomplished by the NSA, but they can’t share their tech with the FBI because it would end up in court, which is where the NSA does not want it to be. I still have a hard time believing the FBI can’t do this without Apple’s help.
Joe
Probably because that’s not their actual goal. Nothing about this particular case is consistent and they don’t seem to care. That suggest anything to you?
Part 2, please!
Thank you for the feedback and the encouragement.
Glad to see your take on the “burdensome” aspect that I thought you’d minimized earlier. But I want to push harder still. Damage to users’ trust (Apple’s reputation) could be immediate with the single phone unlock. You and I can both easily see what the world would: that Apple rolling over for this phone raises the chance that it would be forced to for another. (The same is of course true for the recent action against WhatsApp.)
I will also note that in the “NY case,” Judge Orenstein explicitly addressed how Congress failed to extend CALEA to Apple-type situations, so the AWA’s applicability is fatally harmed. In that sense, the FBI’s end-run effort is called out as such and means that the FBI has a higher burden.
Occasionally I hope that a judge will refuse a filing for the inflammatory insinuations made by DoJ, reprimanding them for the BS and giving them 24 hours to re-file. Maybe some lifetime, sigh.
Finally, a lot of what you correctly ID as irrelevant is important in the court of public opinion. This will impact Congress directly and judges indirectly. (“The Supreme Court reads the newspapers” still.) I personally see some opinions disseminated that look like DoJ disinformation campaigns, and that should be strongly condemned for THEIR corrosive effect on democracy.
“a lot of what you correctly ID as irrelevant actually IS important in the court of public opinion”
Absolutely true, and since I think this matter may be decided in the legislature I should have made that more clear. I think, since I’ve buried myself in the legal aspects of the case that I was thinking of things that would be irrelevant to the courts.
“Glad to see your take on the “burdensome” aspect that I thought you’d minimized earlier”
I believe CALEA is the first hurdle the FBI will have to overcome. I believe burdensome is just as big a hurdle.
The potential burdens that Apple will incur can be minimized to a couple of hours of work by a couple of engineers or maximized to draconian consequences of a most dire nature. That’s why I’ve devoting a separate article to the topic. People simply do not understand the potential ramifications of the FBI forcing Apple to create code to defeat their very own encryption.
People seem to be obsessed with details, while the FBi and executive branch are just using them as a distraction. This is exactly the kind of outcome I’ve been expecting since the “War on Terror” was adopted as the flag bearer to crush citizens rights. Unfortunately it won’t just be restricted to the U.S. Why didn’t they call it “War on Terrorism”? It’s only one more little syllable and War on Commun makes as little sense.
This is power like the Nazis (and Stalin of course) could only dream of (and probably did).
The FBI is asserting that the All Writs Act authorizes a court to issue any writ to further lawful investigations by the FBI unless expressly forbidden by an Act of Congress. This seems extremely dangerous reasoning. Federal law was limited by the Founding Fathers to only grant power to the Federal government when the will of the people was expressed by an Act of Congress, signed by the President, and consistent with the limits imposed by the Constitution. Now the FBI believes its power is only limited not by what Congress has granted, but only by what Congress has expressly forbidden. Such power would only be constrained by the imagination of the FBI (or any other law enforcement agency) so long as a judge could be persuaded to issue the writ. This is how this case arrives at the point of the FBI believing it is entitled to compel anyone to do anything, even against their will, to assist the FBI’s activities so long as the Fifth Amendment is not violated. To me this is the most important case to be decided since Gideon v. Wainwright (right to legal counsel). Please do another article as your background as an attorney is extemely helpful.
Yes, this is one of the arguments that Apple is making and it was one of the pillars that Judge Ornstein leaned upon when denying a similar request by the FBI similar in a New York case.
The argument goes like this. The All Writs Act was designed to fill in gaps. But the FBI is not asking the court to fill in gaps in existing legislation, they’re asking the courts to grant them powers DESPITE existing legislation; powers that actually defeat the purpose of existing legislation.
The Department Of Justice says there’s no need to worry because the court’s have a long tradition of using judicial restraint. But whereas before, the courts were guided by trying to fill gaps between existing legislative “peaks”, under the FBI’s interpretation of the All Writs Act, there are virtually not guidelines and, in a worst case scenario, the courts become an independent super legislature. Judge Ornstein said as much:
“Such a broad reading of the statute invites an exercise of judicial activism that is breathtaking in its scope and fundamentally inconsistent with my understanding of the extent of my authority.”
I have strong trust of the judicial system to restrain or prevent governmental overreach. However, the exercise of police power was one of the primary threats to liberty with which the Founding Fathers concerned themselves. Hence fully half of the first Ten Amendments address limits on police power. The greatest threat to a free society is not from enemies outside its borders, but rather it is the abuse of police power by the people’s own government. Compelling one to act against one’s will to aid police power seems to me essential to a police state. While the debate surrounding encryption and privacy is important, I am frustrated that the far greater issue eludes most people. if Apple loses, what lies next? Will the very act of not complying with an FBI request become criminal itself?
You bet. This is not a slippery slope, but a leap into a bottomless void.
That’s exactly what we’re racing towards, and not just in the U.S. Every tinpot sociopath and crime oligarch is salivating at the possibilities, but this will lead us straight to a new dark age that is likely to be unrecoverable.
Footnote 2. Yes.
Joe
Thank you very much for by far the very best discussion on this subject that I have encountered. You make it easy for a person who is not familiar with US law to understand, whilst structuring the argument in a way that gives me confidence that all relevant bases have been covered. This is great.
It’s also great that good articles attract wonderful comments.
Wow, Naofumi, your comment is gracious on so many levels. Thank you so very much for that.
“It’s also great that good articles attract wonderful comments.”
Let me just join with you in saying that the commentators at Techpinions are some of the very best there are on the web.
This is unbelievably serious and heads can’t simply be buried in the sand. The FBi (ironically autocorrected to fib) is the spearhead of the feared dystopian police state and it appears the U.S. Government is pressuring other governments to preempt US legislation by dropping their own first, to rapidly escalate pressure on Apple initially.
For the Apple haters out there, please realise this is just the start. You will all be attacked and monitored, but not just by the so called government.
This is so beyond Apple, that your ‘Apple Haters’ comment is just unnecessary. Do I go around saying the only reason Apple Lovers care is because it involves Apple?
This is too important, and you say so yourself, to let our brand loyalty get involved in any way. It’s just a case study.
There is some nice and utilitarian information on this site.
I think the admin of this site is really working hard for his website since here every stuff is quality based data.
http://withoutprescription.guru/# ed meds online without doctor prescription
prednisone 2 mg: mail order prednisone – prednisone 80 mg daily
https://indiapharm.guru/# online pharmacy india
ed meds online without doctor prescription: ed meds online without doctor prescription – buy prescription drugs
https://indiapharm.guru/# india pharmacy
prednisone 20mg online pharmacy: prednisone brand name canada – can you buy prednisone over the counter in usa
generic sildenafil 92630 where to buy sildenafil in canada sildenafil citrate pfizer
http://levitra.icu/# Buy Levitra 20mg online
http://tadalafil.trade/# online tadalafil prescription
Levitra 20 mg for sale Levitra 10 mg buy online п»їLevitra price
https://sildenafil.win/# sildenafil 50 mg tablet price in india
buy sildenafil 20 mg tablets sildenafil purchase sildenafil best price canada
http://kamagra.team/# Kamagra 100mg price
buy tadalafil 5mg buy tadalafil 100mg tadalafil 20mg uk
http://levitra.icu/# Vardenafil price
buy tadalafil from india buy tadalafil from india cheap tadalafil 5mg
can you buy zithromax over the counter in australia: zithromax z-pak – zithromax for sale us
lisinopril brand name canada Over the counter lisinopril lisinopril with out prescription
zithromax 500 price: buy cheap generic zithromax – zithromax online
doxycycline 40 mg generic: doxycycline buy online – buy doxycycline 100mg canada
doxycycline over the counter canada Doxycycline 100mg buy online doxycycline brand name india
amoxicillin 500mg no prescription: amoxil for sale – can you purchase amoxicillin online
buy zithromax online cheap: buy cheap generic zithromax – zithromax 600 mg tablets
doxycycline 50mg tablets Buy doxycycline for chlamydia doxycycline tablets canada
amoxicillin buy no prescription: purchase amoxicillin online – can you buy amoxicillin over the counter canada
ciprofloxacin over the counter Ciprofloxacin online prescription ciprofloxacin generic price
buy generic ciprofloxacin: ciprofloxacin generic – cipro ciprofloxacin
buy cheap generic zithromax: buy zithromax – generic zithromax online paypal
best lisinopril brand prescription drug prices lisinopril zestoretic 10 12.5 mg
buy lisinopril online usa: Buy Lisinopril 20 mg online – lisinopril drug
medicine in mexico pharmacies: mexican pharmacy online – buying from online mexican pharmacy
pharmacy website india: indian pharmacy – online pharmacy india
medicine in mexico pharmacies: mexican online pharmacy – purple pharmacy mexico price list
reputable mexican pharmacies online: п»їbest mexican online pharmacies – best online pharmacies in mexico
canada drugstore pharmacy rx accredited canadian pharmacy canadian medications
п»їbest mexican online pharmacies: top mail order pharmacy from Mexico – medication from mexico pharmacy
neurontin generic south africa: generic gabapentin – neurontin 300
can i get generic clomid without dr prescription: Buy Clomid Shipped From Canada – can i purchase generic clomid without dr prescription
where buy clomid price: Clomiphene Citrate 50 Mg – can i order generic clomid for sale
can you buy ventolin over the counter uk: buy Ventolin inhaler – where can i buy ventolin over the counter
http://sildenafilit.bid/# miglior sito dove acquistare viagra
migliori farmacie online 2023: kamagra – farmacia online migliore
farmacie on line spedizione gratuita avanafil generico farmaci senza ricetta elenco
http://kamagrait.club/# acquistare farmaci senza ricetta
farmacie on line spedizione gratuita: farmacia online piu conveniente – farmacia online
http://farmaciait.pro/# acquistare farmaci senza ricetta
https://sildenafilit.bid/# dove acquistare viagra in modo sicuro
farmacia online migliore: kamagra – farmacie online autorizzate elenco
https://avanafilit.icu/# farmacia online miglior prezzo
https://farmacia.best/# farmacias online seguras en espaГ±a
п»їfarmacia online comprar kamagra en espana farmacia envГos internacionales
http://farmacia.best/# farmacia online barata
farmacias online seguras comprar cialis original farmacias online seguras
https://kamagraes.site/# farmacia online madrid
farmacia online madrid comprar kamagra en espana farmacias online seguras
https://tadalafilo.pro/# farmacias online seguras
viagra online cerca de malaga sildenafilo 100mg precio farmacia viagra para mujeres
http://tadalafilo.pro/# farmacia online internacional
http://vardenafilo.icu/# farmacia 24h
farmacia online madrid vardenafilo farmacias online seguras en espaГ±a
farmacia online barata cialis en Espana sin receta contrareembolso farmacia 24h
Viagra pas cher livraison rapide france: Acheter du Viagra sans ordonnance – Viagra femme ou trouver
Viagra pas cher livraison rapide france Meilleur Viagra sans ordonnance 24h Viagra gГ©nГ©rique sans ordonnance en pharmacie
pharmacie ouverte 24/24: pharmacie en ligne sans ordonnance – acheter mГ©dicaments Г l’Г©tranger
Pharmacie en ligne livraison 24h pharmacie en ligne sans ordonnance pharmacie ouverte
Sildenafil teva 100 mg sans ordonnance: Acheter du Viagra sans ordonnance – Viagra femme ou trouver
Pharmacie en ligne fiable cialis sans ordonnance acheter mГ©dicaments Г l’Г©tranger
Pharmacies en ligne certifiГ©es: levitra generique prix en pharmacie – Pharmacies en ligne certifiГ©es
Pharmacie en ligne fiable levitra generique prix en pharmacie Pharmacie en ligne fiable
http://viagrakaufen.store/# Sildenafil Preis
https://cialiskaufen.pro/# gГјnstige online apotheke
http://potenzmittel.men/# п»їonline apotheke
https://apotheke.company/# gГјnstige online apotheke
https://viagrakaufen.store/# Viagra kaufen ohne Rezept legal
https://kamagrakaufen.top/# online apotheke preisvergleich
We’re a group of volunteers and opening a new scheme in our community.
Your web site provided us with valuable information to work on. You have done a formidable job and our whole community will be thankful to you.
http://apotheke.company/# online apotheke gГјnstig
http://cialiskaufen.pro/# versandapotheke versandkostenfrei
buying prescription drugs in mexico online mexico drug stores pharmacies mexican drugstore online
https://mexicanpharmacy.cheap/# medication from mexico pharmacy
http://mexicanpharmacy.cheap/# medication from mexico pharmacy
mexican drugstore online reputable mexican pharmacies online mexico pharmacies prescription drugs
https://mexicanpharmacy.cheap/# mexican border pharmacies shipping to usa
http://mexicanpharmacy.cheap/# mexican rx online
What i don’t understood is if truth be told how
you’re no longer really much more smartly-preferred than you might be now.
You’re so intelligent. You know therefore significantly in the case of this subject, produced me personally consider it from
numerous various angles. Its like women and men are not interested except it’s something
to do with Woman gaga! Your individual stuffs great.
At all times deal with it up!
https://mexicanpharmacy.cheap/# mexico pharmacies prescription drugs
https://mexicanpharmacy.cheap/# mexico drug stores pharmacies
buy medicines online in india Online medicine order – п»їlegitimate online pharmacies india indiapharmacy.guru
best rated canadian pharmacy canadian drugs pharmacy – canadian pharmacy world canadiandrugs.tech
canadian pharmacy india top 10 online pharmacy in india – india pharmacy indiapharmacy.guru
reputable indian pharmacies reputable indian pharmacies – buy medicines online in india indiapharmacy.guru
cures for ed treatments for ed what are ed drugs edpills.tech
reputable indian online pharmacy indianpharmacy com – online shopping pharmacy india indiapharmacy.guru
legit canadian pharmacy online buy drugs from canada – safe reliable canadian pharmacy canadiandrugs.tech
ed pills online otc ed pills – best ed treatment edpills.tech
http://mexicanpharmacy.company/# mexico pharmacy mexicanpharmacy.company
canadian pharmacy review canadian pharmacy no scripts – online canadian pharmacy canadiandrugs.tech
india online pharmacy best india pharmacy – top 10 online pharmacy in india indiapharmacy.guru
https://ciprofloxacin.life/# buy cipro
3000mg prednisone prednisone for cheap prednisone pharmacy
https://clomid.site/# where to buy generic clomid
https://clomid.site/# where to get clomid
http://amoxil.icu/# order amoxicillin online
http://prednisone.bid/# prednisone generic brand name
cipro ciprofloxacin: ciprofloxacin over the counter – cipro online no prescription in the usa
http://clomid.site/# can i purchase clomid without prescription
buy generic zithromax online: azithromycin zithromax – where can i buy zithromax medicine
buy misoprostol over the counter: buy cytotec – cytotec buy online usa
nolvadex d: tamoxifen bone pain – tamoxifen and weight loss
http://zithromaxbestprice.icu/# buy zithromax online fast shipping
http://zithromaxbestprice.icu/# zithromax pill
cytotec pills buy online: cytotec pills buy online – buy cytotec in usa
buy misoprostol over the counter Cytotec 200mcg price cytotec pills buy online
https://nolvadex.fun/# nolvadex pct
buy cytotec online fast delivery: buy cytotec over the counter – buy cytotec over the counter
order doxycycline 100mg without prescription: doxycycline order online – buy doxycycline online uk
tamoxifen lawsuit: nolvadex online – nolvadex 20mg
https://lisinoprilbestprice.store/# lisinopril 10 mg tablets price
https://nolvadex.fun/# tamoxifen breast cancer
buy cytotec pills online cheap: buy cytotec – buy cytotec
http://doxycyclinebestprice.pro/# doxycycline 500mg
generic zithromax india buy zithromax zithromax over the counter
cytotec pills buy online: buy cytotec – Misoprostol 200 mg buy online
http://nolvadex.fun/# tamoxifen rash pictures
generic zithromax india: how much is zithromax 250 mg – buy zithromax online cheap
http://zithromaxbestprice.icu/# can you buy zithromax over the counter in canada
Cytotec 200mcg price: Misoprostol 200 mg buy online – cytotec online
lisinopril 80 medicine lisinopril 10 mg lisinopril 20 mg price without prescription
https://cytotec.icu/# buy cytotec over the counter
tamoxifen side effects forum: nolvadex during cycle – tamoxifen vs clomid
http://mexicopharm.com/# mexico pharmacy mexicopharm.com
medicine in mexico pharmacies Best pharmacy in Mexico п»їbest mexican online pharmacies mexicopharm.com
medication from mexico pharmacy: Medicines Mexico – mexico drug stores pharmacies mexicopharm.com
best online pharmacies in mexico: mexican pharmacy – reputable mexican pharmacies online mexicopharm.com
buy prescription drugs from india: India pharmacy of the world – п»їlegitimate online pharmacies india indiapharm.llc
indian pharmacy: Online India pharmacy – mail order pharmacy india indiapharm.llc
http://indiapharm.llc/# best india pharmacy indiapharm.llc
mexican border pharmacies shipping to usa: reputable mexican pharmacies online – mexican rx online mexicopharm.com
http://mexicopharm.com/# mexican drugstore online mexicopharm.com
п»їlegitimate online pharmacies india indian pharmacy to usa buy medicines online in india indiapharm.llc
mexico drug stores pharmacies: Mexico pharmacy online – buying from online mexican pharmacy mexicopharm.com
https://indiapharm.llc/# mail order pharmacy india indiapharm.llc
mexican mail order pharmacies: mexican pharmacy – buying prescription drugs in mexico mexicopharm.com
medicine in mexico pharmacies: Medicines Mexico – mexican pharmaceuticals online mexicopharm.com
canadian pharmacy: Canadian pharmacy best prices – canadianpharmacyworld canadapharm.life
http://mexicopharm.com/# best mexican online pharmacies mexicopharm.com
best india pharmacy: India Post sending medicines to USA – best online pharmacy india indiapharm.llc
buying prescription drugs in mexico online: Best pharmacy in Mexico – mexico drug stores pharmacies mexicopharm.com
top online pharmacy india indian pharmacy to usa india online pharmacy indiapharm.llc
https://canadapharm.life/# online canadian pharmacy review canadapharm.life
https://mexicopharm.com/# buying prescription drugs in mexico online mexicopharm.com
canadian pharmacies online: Canada Drugs Direct – canadadrugpharmacy com canadapharm.life
buying prescription drugs in mexico: Best pharmacy in Mexico – mexican drugstore online mexicopharm.com
http://mexicopharm.com/# mexican pharmacy mexicopharm.com
п»їbest mexican online pharmacies: Mexico pharmacy online – mexican online pharmacies prescription drugs mexicopharm.com
mexican online pharmacies prescription drugs: purple pharmacy mexico price list – mexican online pharmacies prescription drugs mexicopharm.com
https://levitradelivery.pro/# Cheap Levitra online
tadalafil – generic cheap tadalafil canada tadalafil 2.5 mg generic
Levitra 20 mg for sale: Generic Levitra 20mg – Cheap Levitra online
http://edpillsdelivery.pro/# cheapest ed pills online
cheap ed drugs: ed pills delivery – pills for erection
https://tadalafildelivery.pro/# tadalafil tablets 20 mg india
generic cialis tadalafil: tadalafil mexico – tadalafil price in india
https://edpillsdelivery.pro/# generic ed drugs
can you buy sildenafil over the counter in uk: cheap sildenafil – sildenafil 50mg india
http://levitradelivery.pro/# Cheap Levitra online
https://edpillsdelivery.pro/# ed drugs compared
buy tadalafil 100mg: pharmacy online tadalafil – buy tadalafil 20mg price canada
http://tadalafildelivery.pro/# best price tadalafil 20 mg
Levitra generic best price: Levitra best price – Buy generic Levitra online
where to buy sildenafil over the counter: cheap sildenafil – sildenafil in usa
sildenafil gel caps: Sildenafil price – sildenafil generic usa
http://sildenafildelivery.pro/# sildenafil pills
https://tadalafildelivery.pro/# buy generic tadalafil online uk
tadalafil cialis tadalafil without a doctor prescription tadalafil 20 mg buy online
tadalafil in india online: generic tadalafil daily – tadalafil for sale from india
https://sildenafildelivery.pro/# sildenafil 100mg online india
buy kamagra online usa: buy kamagra – buy kamagra online usa
https://amoxil.guru/# order amoxicillin 500mg
https://clomid.auction/# where to buy cheap clomid online
how can i get clomid for sale: cheapest clomid – can i get cheap clomid online
п»їpaxlovid paxlovid india Paxlovid over the counter
https://prednisone.auction/# prednisone without a prescription
http://stromectol.guru/# ivermectin 0.2mg
https://paxlovid.guru/# paxlovid price
https://prednisone.auction/# prednisone 20mg prescription cost
paxlovid pharmacy: buy paxlovid online – Paxlovid over the counter
http://amoxil.guru/# where can i buy amoxocillin
https://amoxil.guru/# amoxicillin 875 125 mg tab
http://stromectol.guru/# ivermectin 0.5% brand name
SightCare supports overall eye health, enhances vision, and protects against oxidative stress. Take control of your eye health and enjoy the benefits of clear and vibrant eyesight with Sight Care. https://sightcarebuynow.us/
http://clomid.auction/# cheap clomid without rx
buying prednisone without prescription: prednisone – prednisone best prices
https://amoxil.guru/# where can i buy amoxicillin without prec
paxlovid generic buy paxlovid online paxlovid pill
http://amoxil.guru/# can you buy amoxicillin over the counter in canada
http://prednisone.auction/# cheapest prednisone no prescription
http://clomid.auction/# how can i get clomid
prednisone cream: generic prednisone for sale – 10 mg prednisone
https://finasteride.men/# cost generic propecia online
cytotec online: buy cytotec online – cytotec abortion pill
http://lisinopril.fun/# lisinopril cheap price
order propecia without a prescription: buy propecia – cost propecia without rx
https://finasteride.men/# order generic propecia
cost of propecia pill: Finasteride buy online – cost generic propecia without rx
http://azithromycin.store/# zithromax cost canada
lasix Over The Counter Lasix buy furosemide online
cost generic propecia pills: Cheapest finasteride online – buying cheap propecia without prescription
https://finasteride.men/# order generic propecia
generic lasix: lasix 40mg – furosemide 100 mg
http://furosemide.pro/# lasix tablet
https://furosemide.pro/# lasix 100mg
lasix 100 mg Over The Counter Lasix lasix furosemide
get generic propecia price: Buy finasteride 1mg – buying generic propecia pills
https://misoprostol.shop/# cytotec online
generic zestoretic: buy lisinopril online – lisinopril 80 mg
http://furosemide.pro/# furosemida
zithromax capsules 250mg: zithromax over the counter uk – zithromax capsules 250mg
lasix online Buy Lasix lasix generic name
order propecia without insurance: Buy finasteride 1mg – get generic propecia tablets
http://misoprostol.shop/# buy cytotec pills online cheap
furosemide 40 mg: Buy Furosemide – lasix 40 mg
can you buy zithromax over the counter in mexico: buy zithromax z-pak online – how to get zithromax
https://misoprostol.shop/# buy cytotec pills online cheap
https://lisinopril.fun/# otc lisinopril
http://lisinopril.fun/# drug lisinopril
lisinopril 20mg india: lisinopril 5mg cost – lisinopril 5mg pill
lasix online Buy Furosemide generic lasix
https://misoprostol.shop/# cytotec pills online
buy zithromax without prescription online: buy zithromax z-pak online – zithromax for sale us
cheap propecia without a prescription: Finasteride buy online – cost of propecia
furosemida: Buy Lasix – furosemide 100mg
http://misoprostol.shop/# purchase cytotec
http://misoprostol.shop/# buy misoprostol over the counter
how to buy zithromax online cheapest azithromycin zithromax buy online
http://misoprostol.shop/# buy cytotec online
buy cytotec in usa: Misoprostol best price in pharmacy – buy cytotec online fast delivery
http://lisinopril.fun/# lisinopril pill
farmacia online migliore: Avanafil farmaco – farmacie online sicure
farmacie online sicure: avanafil – farmacia online
http://farmaciaitalia.store/# farmacia online migliore
alternativa al viagra senza ricetta in farmacia alternativa al viagra senza ricetta in farmacia viagra online spedizione gratuita
farmacie online sicure: farmacia online spedizione gratuita – top farmacia online
https://farmaciaitalia.store/# farmacia online piГ№ conveniente
farmacie online autorizzate elenco: comprare avanafil senza ricetta – acquisto farmaci con ricetta
http://avanafilitalia.online/# farmacia online migliore
viagra generico in farmacia costo: viagra online siti sicuri – viagra originale recensioni
farmacia online piГ№ conveniente: kamagra oral jelly consegna 24 ore – farmacia online senza ricetta
https://avanafilitalia.online/# п»їfarmacia online migliore
farmacie online affidabili cialis generico consegna 48 ore acquistare farmaci senza ricetta
http://avanafilitalia.online/# farmacie online sicure
п»їfarmacia online migliore: Tadalafil generico – п»їfarmacia online migliore
http://sildenafilitalia.men/# viagra ordine telefonico
farmacia online piГ№ conveniente: comprare avanafil senza ricetta – comprare farmaci online all’estero
https://kamagraitalia.shop/# farmacia online piГ№ conveniente
farmacia online senza ricetta avanafil prezzo farmacie on line spedizione gratuita
http://kamagraitalia.shop/# farmacie online autorizzate elenco
farmaci senza ricetta elenco: farmacia online piГ№ conveniente – farmacia online senza ricetta
https://kamagraitalia.shop/# farmacie on line spedizione gratuita
farmacie online sicure: farmacia online spedizione gratuita – farmacia online senza ricetta
http://kamagraitalia.shop/# farmacia online più conveniente
farmacia online miglior prezzo: cialis generico – п»їfarmacia online migliore
https://sildenafilitalia.men/# dove acquistare viagra in modo sicuro
farmacie on line spedizione gratuita kamagra gold farmacia online senza ricetta
http://farmaciaitalia.store/# farmaci senza ricetta elenco
viagra generico recensioni: viagra prezzo – alternativa al viagra senza ricetta in farmacia
Online medicine order: indian pharmacies safe – best india pharmacy
https://canadapharm.shop/# best rated canadian pharmacy
https://mexicanpharm.store/# buying prescription drugs in mexico online
mexican pharmaceuticals online п»їbest mexican online pharmacies pharmacies in mexico that ship to usa
the canadian drugstore: cheap canadian pharmacy online – legitimate canadian mail order pharmacy
http://canadapharm.shop/# canadapharmacyonline legit
mexican pharmaceuticals online: mexican border pharmacies shipping to usa – pharmacies in mexico that ship to usa
indianpharmacy com: indianpharmacy com – top 10 pharmacies in india
https://indiapharm.life/# indian pharmacy online
http://mexicanpharm.store/# mexican rx online
canadian neighbor pharmacy: canadian pharmacy king – canadian pharmacy 365
http://mexicanpharm.store/# mexican pharmaceuticals online
canadian drugs online ordering drugs from canada best canadian pharmacy online
mexican mail order pharmacies: pharmacies in mexico that ship to usa – mexican border pharmacies shipping to usa
mexican border pharmacies shipping to usa: reputable mexican pharmacies online – buying from online mexican pharmacy
https://indiapharm.life/# top 10 online pharmacy in india
Online medicine order: india pharmacy – п»їlegitimate online pharmacies india
http://canadapharm.shop/# certified canadian international pharmacy
canada drugs reviews: canadian pharmacy meds – pharmacy canadian superstore
http://canadapharm.shop/# canadian pharmacy online reviews
https://indiapharm.life/# india online pharmacy
indian pharmacy: indian pharmacies safe – reputable indian online pharmacy
online canadian pharmacy: online canadian pharmacy reviews – canadian drug pharmacy
best canadian pharmacy: legitimate canadian pharmacy online – canadian discount pharmacy
https://canadapharm.shop/# canadian pharmacy meds review
canadian discount pharmacy canadian pharmacy uk delivery ed meds online canada
п»їlegitimate online pharmacies india: reputable indian online pharmacy – п»їlegitimate online pharmacies india
https://canadapharm.shop/# best online canadian pharmacy
mexico drug stores pharmacies: medication from mexico pharmacy – mexican online pharmacies prescription drugs
my canadian pharmacy: canadian family pharmacy – best canadian online pharmacy
https://indiapharm.life/# indianpharmacy com
canadian pharmacy king: canadian pharmacy meds review – best canadian online pharmacy
https://indiapharm.life/# world pharmacy india
canadian pharmacies comparison: the canadian drugstore – reliable canadian pharmacy
reputable indian pharmacies online pharmacy india Online medicine order
http://indiapharm.life/# reputable indian pharmacies
canadian pharmacy mall: maple leaf pharmacy in canada – buying from canadian pharmacies
http://clomidpharm.shop/# clomid sale
Abortion pills online buy cytotec pills cytotec online
cytotec online: buy cytotec over the counter – cytotec abortion pill
http://prednisonepharm.store/# how to get prednisone without a prescription
buy zithromax online fast shipping: zithromax online pharmacy canada – can you buy zithromax over the counter in canada
http://zithromaxpharm.online/# purchase zithromax z-pak
tamoxifen and antidepressants: nolvadex estrogen blocker – nolvadex for pct
https://prednisonepharm.store/# buy prednisone no prescription
tamoxifen citrate what is tamoxifen used for tamoxifen and antidepressants
http://cytotec.directory/# buy misoprostol over the counter
prednisone 10: no prescription prednisone canadian pharmacy – price of prednisone tablets
http://zithromaxpharm.online/# azithromycin zithromax
zithromax 500 without prescription: buy zithromax 500mg online – can i buy zithromax over the counter
https://nolvadex.pro/# tamoxifen estrogen
tamoxifen skin changes: tamoxifen and weight loss – nolvadex generic
https://prednisonepharm.store/# prednisone in canada
can i purchase clomid without insurance: where to buy clomid no prescription – how can i get clomid without insurance
They provide a global perspective on local health issues http://cytotec.directory/# Misoprostol 200 mg buy online
http://prednisonepharm.store/# 5 prednisone in mexico
non prescription ed drugs: best non prescription ed pills – ed meds online without prescription or membership
levitra without a doctor prescription: best non prescription ed pills – tadalafil without a doctor’s prescription
http://edwithoutdoctorprescription.store/# viagra without a doctor prescription walmart
canada online pharmacy reviews https://edpills.bid/# cheap erectile dysfunction
online discount pharmacy
levitra without a doctor prescription: non prescription ed pills – sildenafil without a doctor’s prescription
https://reputablepharmacies.online/# cheapest canadian pharmacies
https://edwithoutdoctorprescription.store/# buy prescription drugs online legally
erectile dysfunction medicines: ed medications list – best medication for ed
https://edwithoutdoctorprescription.store/# prescription drugs without doctor approval
pills for erection: ed drug prices – ed treatment review
pharmacies withour prescriptions http://edwithoutdoctorprescription.store/# non prescription ed pills
canada pharmacy online no prescription
best canadian pharmacy cialis: discount drugs online – canadian drug mart pharmacy
pain meds online without doctor prescription my canadian pharmacy rx canadian pharmacy prescription
http://reputablepharmacies.online/# no perscription pharmacy
medicine for erectile: best male ed pills – natural remedies for ed
testosterone canadian pharmacy buy prescription drugs online legally prednisone mexican pharmacy
http://edwithoutdoctorprescription.store/# ed meds online without doctor prescription
https://edpills.bid/# best ed pills non prescription
generic ed pills: new ed treatments – best medication for ed
legal to buy prescription drugs from canada: non prescription ed drugs – buy prescription drugs from canada cheap
prescription drugs online without doctor: best ed pills non prescription – buy prescription drugs without doctor
https://edwithoutdoctorprescription.store/# buy prescription drugs from india
prescription drugs online without doctor ed meds online without doctor prescription buy prescription drugs online without
buy cheap prescription drugs online: sildenafil without a doctor’s prescription – real viagra without a doctor prescription usa
canadian pharmacy no rx needed buy prescription drugs online my canadian drug store
https://reputablepharmacies.online/# online prescription
https://mexicanpharmacy.win/# best online pharmacies in mexico mexicanpharmacy.win
safe online pharmacies
mexican mail order pharmacies: mexican online pharmacies prescription drugs – pharmacies in mexico that ship to usa mexicanpharmacy.win
http://canadianpharmacy.pro/# drugs from canada canadianpharmacy.pro
indian pharmacy: international medicine delivery from india – buy medicines online in india indianpharmacy.shop
http://indianpharmacy.shop/# Online medicine home delivery indianpharmacy.shop
Hey! I’m at work browsing your blog from my new apple iphone!
Just wanted to say I love reading through your blog
and look forward to all your posts! Keep up the great work!
http://canadianpharmacy.pro/# canadadrugpharmacy com canadianpharmacy.pro
world pharmacy india: Cheapest online pharmacy – mail order pharmacy india indianpharmacy.shop
http://indianpharmacy.shop/# best india pharmacy indianpharmacy.shop
canadian pharmacy without prescription
https://canadianpharmacy.pro/# canadian pharmacy checker canadianpharmacy.pro
online pharmacy india Best Indian pharmacy indianpharmacy com indianpharmacy.shop
http://indianpharmacy.shop/# indian pharmacy paypal indianpharmacy.shop
https://indianpharmacy.shop/# top 10 online pharmacy in india indianpharmacy.shop
http://indianpharmacy.shop/# reputable indian pharmacies indianpharmacy.shop
india pharmacy international medicine delivery from india top 10 online pharmacy in india indianpharmacy.shop
http://indianpharmacy.shop/# buy prescription drugs from india indianpharmacy.shop
top 10 pharmacies in india
https://indianpharmacy.shop/# pharmacy website india indianpharmacy.shop
http://indianpharmacy.shop/# indian pharmacies safe indianpharmacy.shop
п»їlegitimate online pharmacies india
best canadian online pharmacy reviews Canadian pharmacy online canadian pharmacies canadianpharmacy.pro
http://mexicanpharmacy.win/# buying prescription drugs in mexico mexicanpharmacy.win
canada medicine
https://mexicanpharmacy.win/# purple pharmacy mexico price list mexicanpharmacy.win
https://canadianpharmacy.pro/# canadian pharmacies comparison canadianpharmacy.pro
indian pharmacies safe
indian pharmacies safe indian pharmacy to usa п»їlegitimate online pharmacies india indianpharmacy.shop
http://mexicanpharmacy.win/# buying prescription drugs in mexico mexicanpharmacy.win
http://mexicanpharmacy.win/# mexico pharmacies prescription drugs mexicanpharmacy.win
http://mexicanpharmacy.win/# best online pharmacies in mexico mexicanpharmacy.win
buy medicines online in india
https://mexicanpharmacy.win/# mexican pharmaceuticals online mexicanpharmacy.win
mexican pharmacy list
buying from online mexican pharmacy online mexican pharmacy medicine in mexico pharmacies mexicanpharmacy.win
https://mexicanpharmacy.win/# buying from online mexican pharmacy mexicanpharmacy.win
http://mexicanpharmacy.win/# mexico drug stores pharmacies mexicanpharmacy.win
pharmacy website india
Online medicine order Order medicine from India to USA indian pharmacy online indianpharmacy.shop
https://canadianpharmacy.pro/# legitimate canadian pharmacy online canadianpharmacy.pro
https://indianpharmacy.shop/# reputable indian pharmacies indianpharmacy.shop
reputable indian pharmacies
indian pharmacy online international medicine delivery from india best online pharmacy india indianpharmacy.shop
http://mexicanpharmacy.win/# buying from online mexican pharmacy mexicanpharmacy.win
https://canadianpharmacy.pro/# canadian pharmacy no scripts canadianpharmacy.pro
http://indianpharmacy.shop/# top 10 online pharmacy in india indianpharmacy.shop
online pharmacy india
Pharmacie en ligne livraison 24h levitra generique Pharmacie en ligne pas cher
Meilleur Viagra sans ordonnance 24h: viagrasansordonnance.pro – Prix du Viagra 100mg en France
https://levitrasansordonnance.pro/# Pharmacies en ligne certifiées
Pharmacie en ligne fiable PharmaDoc pharmacie ouverte 24/24
Pharmacie en ligne sans ordonnance: kamagra livraison 24h – Pharmacie en ligne livraison 24h
acheter mГ©dicaments Г l’Г©tranger: kamagra livraison 24h – Pharmacie en ligne livraison 24h
https://pharmadoc.pro/# acheter mГ©dicaments Г l’Г©tranger
Pharmacie en ligne fiable
https://cialissansordonnance.shop/# Pharmacie en ligne pas cher
pharmacie ouverte 24/24 PharmaDoc Pharmacie en ligne livraison rapide
Acheter mГ©dicaments sans ordonnance sur internet: pharmacie en ligne sans ordonnance – acheter medicament a l etranger sans ordonnance
https://viagrasansordonnance.pro/# Viagra sans ordonnance livraison 48h
Acheter mГ©dicaments sans ordonnance sur internet pharmacie en ligne sans ordonnance п»їpharmacie en ligne
http://pharmadoc.pro/# Pharmacie en ligne livraison 24h
Pharmacie en ligne fiable: Acheter mГ©dicaments sans ordonnance sur internet – Pharmacie en ligne pas cher
https://levitrasansordonnance.pro/# Pharmacie en ligne pas cher
Acheter mГ©dicaments sans ordonnance sur internet
acheter medicament a l etranger sans ordonnance: acheter medicament a l etranger sans ordonnance – acheter mГ©dicaments Г l’Г©tranger
Pharmacie en ligne livraison gratuite cialis generique Pharmacie en ligne pas cher
Viagra prix pharmacie paris: Viagra sans ordonnance 24h – Viagra sans ordonnance pharmacie France
http://levitrasansordonnance.pro/# Pharmacies en ligne certifiées
Acheter mГ©dicaments sans ordonnance sur internet: kamagra en ligne – Pharmacies en ligne certifiГ©es
http://viagrasansordonnance.pro/# Viagra pas cher livraison rapide france
п»їpharmacie en ligne acheterkamagra.pro Pharmacie en ligne fiable
Pharmacie en ligne fiable: pharmacie en ligne – Pharmacie en ligne livraison gratuite
http://viagrasansordonnance.pro/# Sildénafil 100 mg sans ordonnance
cheap prednisone 20 mg prednisone otc price where can you buy prednisone
buy prednisone 5mg canada: prednisone prices – prednisone brand name
https://azithromycin.bid/# zithromax prescription in canada
prednisone 50 mg tablet cost: compare prednisone prices – prednisone online
prednisone 20mg prices prednisone 10mg buy online brand prednisone
http://ivermectin.store/# oral ivermectin cost
order stromectol online: ivermectin 500mg – stromectol for sale
https://azithromycin.bid/# zithromax online australia
ivermectin topical: stromectol buy – ivermectin 3mg tablets price
amoxicillin 800 mg price purchase amoxicillin online without prescription generic amoxicillin 500mg
http://clomiphene.icu/# can i order cheap clomid pills
zithromax 250 mg: zithromax for sale us – zithromax 500 mg lowest price drugstore online
ivermectin brand ivermectin buy canada stromectol order
http://ivermectin.store/# ivermectin 4
how can i get generic clomid for sale: where to buy generic clomid online – cost clomid price
how can i get cheap clomid online: can i buy cheap clomid for sale – can you buy clomid without a prescription
http://clomiphene.icu/# cheap clomid for sale
can i purchase prednisone without a prescription prednisone generic brand name prednisone 2.5 mg tab
https://clomiphene.icu/# get clomid tablets
can i buy cheap clomid online: where to buy generic clomid without dr prescription – order cheap clomid without rx
buy zithromax online australia: zithromax buy online – buy zithromax online fast shipping
https://ivermectin.store/# stromectol south africa
zithromax over the counter uk generic zithromax azithromycin zithromax buy
where to buy zithromax in canada: can i buy zithromax over the counter in canada – zithromax 500 mg
https://azithromycin.bid/# where to get zithromax
ivermectin 24 mg ivermectin cream 5% stromectol tablets for humans for sale
https://azithromycin.bid/# zithromax 250mg
Every time I read one of your posts, I come away with something new and interesting to think about. Thanks for consistently putting out such great content!
where can i buy amoxicillin without prec: generic amoxil 500 mg – order amoxicillin online
https://amoxicillin.bid/# amoxicillin capsule 500mg price
canadian pharmacy meds Canadian Pharmacy canadian pharmacy tampa canadianpharm.store
buying prescription drugs in mexico: Certified Pharmacy from Mexico – mexico drug stores pharmacies mexicanpharm.shop
https://canadianpharm.store/# legitimate canadian pharmacy canadianpharm.store
п»їbest mexican online pharmacies: Online Pharmacies in Mexico – mexican online pharmacies prescription drugs mexicanpharm.shop
pharmacies in mexico that ship to usa purple pharmacy mexico price list purple pharmacy mexico price list mexicanpharm.shop
mexican mail order pharmacies: mexico drug stores pharmacies – mexico pharmacies prescription drugs mexicanpharm.shop
http://canadianpharm.store/# real canadian pharmacy canadianpharm.store
http://mexicanpharm.shop/# mexican online pharmacies prescription drugs mexicanpharm.shop
indian pharmacies safe: Indian pharmacy to USA – top 10 pharmacies in india indianpharm.store
canadian compounding pharmacy: Best Canadian online pharmacy – canada rx pharmacy world canadianpharm.store
canadian drug Licensed Online Pharmacy canadianpharmacymeds canadianpharm.store
http://mexicanpharm.shop/# best online pharmacies in mexico mexicanpharm.shop
vipps approved canadian online pharmacy: Canada Pharmacy online – canadian pharmacy 24h com safe canadianpharm.store
medication from mexico pharmacy Certified Pharmacy from Mexico medication from mexico pharmacy mexicanpharm.shop
Your words are powerful and have the ability to make a real difference in people’s lives Keep using your voice to spread positivity and knowledge
The design and layout of this blog are so aesthetically pleasing and user-friendly It’s a pleasure to navigate through
world pharmacy india: order medicine from india to usa – best online pharmacy india indianpharm.store
http://canadianpharm.store/# canadian online drugstore canadianpharm.store
buy medicines online in india: top 10 online pharmacy in india – online pharmacy india indianpharm.store
pharmacy wholesalers canada trusted canadian pharmacy canadian pharmacy antibiotics canadianpharm.store
http://mexicanpharm.shop/# pharmacies in mexico that ship to usa mexicanpharm.shop
п»їbest mexican online pharmacies: Online Pharmacies in Mexico – buying prescription drugs in mexico mexicanpharm.shop
medication from mexico pharmacy: Online Mexican pharmacy – medicine in mexico pharmacies mexicanpharm.shop
http://mexicanpharm.shop/# buying from online mexican pharmacy mexicanpharm.shop
canadian pharmacy 365: Canada Pharmacy online – reddit canadian pharmacy canadianpharm.store
http://indianpharm.store/# top online pharmacy india indianpharm.store
indianpharmacy com order medicine from india to usa top 10 online pharmacy in india indianpharm.store
mexican pharmaceuticals online: Certified Pharmacy from Mexico – buying from online mexican pharmacy mexicanpharm.shop
legit canadian pharmacy: Canada Pharmacy online – buy prescription drugs from canada cheap canadianpharm.store
https://mexicanpharm.shop/# mexican border pharmacies shipping to usa mexicanpharm.shop
medication from mexico pharmacy Certified Pharmacy from Mexico purple pharmacy mexico price list mexicanpharm.shop
legal canadian pharmacy online: Pharmacies in Canada that ship to the US – best canadian online pharmacy reviews canadianpharm.store
https://indianpharm.store/# indian pharmacy paypal indianpharm.store
mexican rx online: buying prescription drugs in mexico online – mexico pharmacies prescription drugs mexicanpharm.shop
mexican pharmaceuticals online: buying from online mexican pharmacy – purple pharmacy mexico price list mexicanpharm.shop
https://canadianpharm.store/# buy canadian drugs canadianpharm.store
https://mexicanpharm.shop/# mexican rx online mexicanpharm.shop
pharmacy website india: Indian pharmacy to USA – cheapest online pharmacy india indianpharm.store
very informative articles or reviews at this time.
india online pharmacy: order medicine from india to usa – mail order pharmacy india indianpharm.store
https://indianpharm.store/# reputable indian online pharmacy indianpharm.store
online shopping pharmacy india Indian pharmacy to USA india pharmacy mail order indianpharm.store
mexican mail order pharmacies: mexican drugstore online – pharmacies in mexico that ship to usa mexicanpharm.shop
mexican pharmaceuticals online: best online pharmacies in mexico – medicine in mexico pharmacies mexicanpharm.shop
http://canadianpharm.store/# canadapharmacyonline com canadianpharm.store
reputable indian pharmacies indian pharmacy online mail order pharmacy india indianpharm.store
safe reliable canadian pharmacy: Canada Pharmacy online – canadian drugs canadianpharm.store
https://mexicanpharm.shop/# mexican rx online mexicanpharm.shop
https://canadianpharm.store/# canadian online drugstore canadianpharm.store
world pharmacy india international medicine delivery from india indianpharmacy com indianpharm.store
best india pharmacy: Indian pharmacy to USA – indian pharmacy online indianpharm.store
I have been struggling with this issue for a while and your post has provided me with much-needed guidance and clarity Thank you so much
most trusted online pharmacy canadian pharmaceuticals canadian pharmacies recommended by aarp
canadian mail order drug companies: canada pharmacy online reviews – cheapest drug prices
https://canadadrugs.pro/# best mail order pharmacies
legitimate canadian pharmacy: canadian drugstore reviews – online pharmacy no prescriptions
non prescription on line pharmacies reliable canadian pharmacy legitimate canadian pharmacy
international pharmacies that ship to the usa: canadian pharmacy testosterone – reputable canadian pharmacy online
canadian pharmacy: pharmacy canada online – superstore pharmacy online
https://canadadrugs.pro/# canada medications
buying prescription drugs canada: canadian prescription prices – canada pharmacy not requiring prescription
legitimate canadian pharmacies online india online pharmacy compare pharmacy prices
http://canadadrugs.pro/# compare medication prices
best online pharmacies canada: canadian drug companies – approved canadian pharmacies online
aarp recommended canadian online pharmacies: safe canadian internet pharmacies – legit canadian pharmacy online
canadian pharmacy reviews canadian online pharmacies buy prescription drugs canada
https://canadadrugs.pro/# canadian pharmacy online
drugs without prescription: canadian drug store viagra – discount online pharmacy
most reputable canadian pharmacy: canada pharmacies online – the generics pharmacy online delivery
http://canadadrugs.pro/# canadian drug store online
canadian pharmacy testosterone gel: family pharmacy online – cheap online pharmacy
canada prescription: pharcharmy online no script – amazon pharmacy drug prices
http://canadadrugs.pro/# top rated canadian online pharmacy
mail order drugs without a prescription: cheapest canadian pharmacy – order canadian drugs
order canadian drugs: list of canadian online pharmacies – online canadian pharmacy with prescription
https://canadadrugs.pro/# mexico pharmacy order online
canada pharmacy: top online pharmacies – canada rx pharmacy
https://canadadrugs.pro/# canadian pharmacies that ship to usa
no script pharmacy: drugs online – top rated online pharmacy
canada pharmacies without script: canada pharmacies online – internet pharmacy
http://canadadrugs.pro/# international pharmacy
canada pharmacies online pharmacy: my mexican drugstore – no prescription rx medicine
canadian wholesale pharmacy: best internet pharmacies – internet pharmacies
https://canadadrugs.pro/# canadian pharmacy online review
canada online pharmacy reviews online prescription pharmacy price comparison
canadian pharmaceuticals for usa sales: discount drugs canada – canadian pharmacy tadalafil
http://canadadrugs.pro/# canadian discount online pharmacy
real viagra without a doctor prescription online prescription for ed meds ed meds online without doctor prescription
non prescription erection pills: erection pills viagra online – new ed drugs
http://canadianinternationalpharmacy.pro/# canadian pharmacy reviews
buying prescription drugs in mexico online: pharmacies in mexico that ship to usa – mexico drug stores pharmacies
top 10 pharmacies in india online pharmacy india top 10 online pharmacy in india
canadian drugs: best online canadian pharmacy – canadian pharmacy india
http://certifiedpharmacymexico.pro/# mexico drug stores pharmacies
http://edwithoutdoctorprescription.pro/# buy prescription drugs without doctor
medication canadian pharmacy: buy drugs from canada – canadian online pharmacy reviews
erectile dysfunction drug best ed drugs ed pills that really work
http://medicinefromindia.store/# online shopping pharmacy india
mexican rx online mexico drug stores pharmacies mexico pharmacies prescription drugs
This is exactly what I needed to read today Your words have provided me with much-needed reassurance and comfort
https://edwithoutdoctorprescription.pro/# viagra without a doctor prescription
ed pills online: top ed pills – ed drugs list
Sumatra Slim Belly Tonic is a unique weight loss supplement that sets itself apart from others in the market. Unlike other supplements that rely on caffeine and stimulants to boost energy levels, Sumatra Slim Belly Tonic takes a different approach. It utilizes a blend of eight natural ingredients to address the root causes of weight gain. By targeting inflammation and improving sleep quality, Sumatra Slim Belly Tonic provides a holistic solution to weight loss. These natural ingredients not only support healthy inflammation but also promote better sleep, which are crucial factors in achieving weight loss goals. By addressing these underlying issues, Sumatra Slim Belly Tonic helps individuals achieve sustainable weight loss results.
cheap canadian pharmacy online pharmacies in canada that ship to the us canadian pharmacy online
http://certifiedpharmacymexico.pro/# pharmacies in mexico that ship to usa
maple leaf pharmacy in canada: canadian pharmacy no scripts – pharmacy wholesalers canada
mexican pharmacy without prescription non prescription ed pills legal to buy prescription drugs from canada
https://canadianinternationalpharmacy.pro/# canada discount pharmacy
http://medicinefromindia.store/# top 10 online pharmacy in india
india pharmacy: reputable indian online pharmacy – indian pharmacy
canadian pharmacy sarasota prescription drugs canada buy online canadian pharmacy ratings
mexican pharmaceuticals online: medicine in mexico pharmacies – mexico drug stores pharmacies
http://edwithoutdoctorprescription.pro/# legal to buy prescription drugs from canada
cures for ed best pills for ed cheap ed pills
Your blog post was fantastic, thanks for the great content!
https://canadianinternationalpharmacy.pro/# canadian pharmacy 365
non prescription ed drugs cialis without a doctor prescription prescription drugs
http://edwithoutdoctorprescription.pro/# prescription drugs online without
Sugar Defender stands as a beacon of natural, side-effect-free blood sugar support. Crafted from a blend of pure, plant-based ingredients, this formula not only helps regulate blood sugar levels but also empowers you on your journey to weight loss, increased vitality, and overall life improvement.
http://medicinefromindia.store/# buy medicines online in india
online pharmacy canada buying drugs from canada reputable canadian online pharmacies
ed prescription drugs: cheap cialis – prescription drugs without doctor approval
http://medicinefromindia.store/# top online pharmacy india
canadapharmacyonline com canada drugs my canadian pharmacy rx
https://canadianinternationalpharmacy.pro/# legit canadian pharmacy
canadian medications canadian mail order pharmacy canadian pharmacy online
This is exactly what I needed to read today Your words have provided me with much-needed reassurance and comfort
https://edwithoutdoctorprescription.pro/# viagra without a doctor prescription walmart
cheap erectile dysfunction pills online: best erectile dysfunction pills – ed pills for sale
best male enhancement pills medicine for impotence best ed drugs
https://canadianinternationalpharmacy.pro/# canadian pharmacy 24h com
cheap ed pills ed treatments best ed medication
https://canadianinternationalpharmacy.pro/# drugs from canada
http://medicinefromindia.store/# buy prescription drugs from india
https://medicinefromindia.store/# buy prescription drugs from india
best canadian online pharmacy canada pharmacy safe canadian pharmacy
medication from mexico pharmacy: п»їbest mexican online pharmacies – medicine in mexico pharmacies
http://certifiedpharmacymexico.pro/# buying from online mexican pharmacy
indian pharmacies safe indian pharmacies safe indian pharmacy paypal
I appreciate how well-researched and informative each post is It’s obvious how much effort you put into your work
The ability of Alpilean to target both subcutaneous and visceral fat distinguishes it from other weight loss products. Subcutaneous fat is visible beneath the skin, whereas visceral fat is harmful fat that accumulates around the organs, increasing the risk of heart disease and other health problems. Alpilean ensures that you not only look better, but also feel better by attacking both types of fat.
http://edpill.cheap/# erection pills that work
reputable indian pharmacies buy medicines online in india reputable indian online pharmacy
Red Boost is a supplement that is meant to improve overall health and well-being, especially in men who may be showing signs of low testosterone. It’s a new product, but it’s already getting a lot of attention because it helps men with common problems that come up as they age.
http://edwithoutdoctorprescription.pro/# ed meds online without doctor prescription
canadian pharmacy 24 com canadian pharmacy meds canadian pharmacy world
buying prescription drugs in mexico: mexican online pharmacies prescription drugs – buying prescription drugs in mexico online
https://medicinefromindia.store/# top 10 online pharmacy in india
Fluxactive Complete’s formulation contains only organic ingredients that have been shown to improve prostate health. These ingredients work together to provide your body with the nutrients it requires. Your overall health improves once your body receives a healthy dose of these nutrients.
purple pharmacy mexico price list purple pharmacy mexico price list buying prescription drugs in mexico
mexican border pharmacies shipping to usa mexico drug stores pharmacies mexican pharmacy
mexican drugstore online buying from online mexican pharmacy best online pharmacies in mexico
best mexican online pharmacies best mexican online pharmacies pharmacies in mexico that ship to usa
mexico pharmacies prescription drugs mexican online pharmacies prescription drugs mexico drug stores pharmacies
mexico pharmacy buying prescription drugs in mexico mexico pharmacy
http://mexicanph.shop/# pharmacies in mexico that ship to usa
mexican border pharmacies shipping to usa
http://mexicanph.shop/# mexican border pharmacies shipping to usa
medicine in mexico pharmacies
mexican mail order pharmacies purple pharmacy mexico price list medicine in mexico pharmacies
mexican pharmaceuticals online buying from online mexican pharmacy mexican drugstore online
mexico pharmacies prescription drugs buying prescription drugs in mexico buying prescription drugs in mexico online
buying prescription drugs in mexico online mexico drug stores pharmacies reputable mexican pharmacies online
mexican drugstore online mexican pharmacy buying from online mexican pharmacy
mexican border pharmacies shipping to usa mexico pharmacy best online pharmacies in mexico
best online pharmacies in mexico buying prescription drugs in mexico online reputable mexican pharmacies online
buying prescription drugs in mexico online buying prescription drugs in mexico online mexico pharmacies prescription drugs
mexican drugstore online mexican online pharmacies prescription drugs medicine in mexico pharmacies
purple pharmacy mexico price list mexican pharmaceuticals online mexico drug stores pharmacies
medication from mexico pharmacy mexican rx online mexican pharmaceuticals online
mexican pharmacy mexican online pharmacies prescription drugs best online pharmacies in mexico
Sugar Defender orchestrates a reduction in blood sugar levels through multifaceted pathways. Its initial impact revolves around enhancing insulin sensitivity, optimizing the body’s efficient use of insulin, ultimately leading to a decrease in blood sugar levels. This proactive strategy works to prevent the storage of glucose as fat, mitigating the risk of developing type 2 diabetes.
mexico pharmacies prescription drugs medication from mexico pharmacy mexican rx online
buying prescription drugs in mexico mexico pharmacies prescription drugs medication from mexico pharmacy
medication from mexico pharmacy mexican border pharmacies shipping to usa mexican pharmacy
buying prescription drugs in mexico mexican border pharmacies shipping to usa mexican border pharmacies shipping to usa
http://mexicanph.com/# mexican online pharmacies prescription drugs
mexico pharmacies prescription drugs
best online pharmacies in mexico purple pharmacy mexico price list purple pharmacy mexico price list
mexican border pharmacies shipping to usa mexico drug stores pharmacies mexican mail order pharmacies
mexican pharmaceuticals online mexico pharmacies prescription drugs medicine in mexico pharmacies
mexican pharmaceuticals online mexican pharmaceuticals online buying from online mexican pharmacy
buying prescription drugs in mexico purple pharmacy mexico price list mexico drug stores pharmacies
http://mexicanph.com/# mexico pharmacies prescription drugs
buying from online mexican pharmacy
mexico drug stores pharmacies mexican border pharmacies shipping to usa medication from mexico pharmacy
mexico drug stores pharmacies mexico pharmacy purple pharmacy mexico price list
https://furosemide.guru/# furosemide
http://amoxil.cheap/# amoxicillin buy no prescription
Sugar Defender’s prowess in managing blood sugar is deeply rooted in its exceptional blend of natural ingredients, each playing a distinct role that contributes to the overall success of the supplement. Here are some noteworthy positive impacts of the Sugar Defender Ingredients blend:
Sugar Defender transcends symptom-focused interventions, delving into the root causes of glucose imbalance. It stands as a dynamic formula that seamlessly aligns with the body’s intrinsic mechanisms, presenting a distinctive and holistic approach to enhancing overall well-being. Beyond a mere supplement, Sugar Defender emerges as a strategic ally in the pursuit of balanced health.
http://stromectol.fun/# stromectol uk
http://furosemide.guru/# furosemide 40 mg
https://lisinopril.top/# lisinopril 49 mg
http://lisinopril.top/# buy lisinopril mexico
https://lisinopril.top/# cost of lisinopril 5 mg
https://lisinopril.top/# zestril 20 mg tablet
Metanail Total Cleanse is our ultimate solution against internal fungus buildup While Metanail Serum Pro fights fungus from the outside, working in perfect sync with the serum,
http://furosemide.guru/# buy furosemide online
http://buyprednisone.store/# prednisone price australia
http://amoxil.cheap/# amoxicillin 500 mg cost
https://amoxil.cheap/# order amoxicillin no prescription
https://stromectol.fun/# order minocycline 100mg
http://lisinopril.top/# zestril 10mg price
Just wanna remark on few general things, The website style is ideal, the topic matter is rattling goodTauranga fences
https://lisinopril.top/# prinivil 25 mg
https://furosemide.guru/# buy furosemide online
https://stromectol.fun/# buy stromectol online uk
http://amoxil.cheap/# buying amoxicillin online
https://lisinopril.top/# how much is lisinopril 5 mg
http://stromectol.fun/# ivermectin 3 mg tabs
http://lisinopril.top/# 1 lisinopril
http://furosemide.guru/# generic lasix
http://buyprednisone.store/# prednisone over the counter uk
https://stromectol.fun/# ivermectin lotion for scabies
http://furosemide.guru/# furosemide 100mg
https://buyprednisone.store/# buying prednisone without prescription
http://buyprednisone.store/# prednisone over the counter south africa
https://stromectol.fun/# ivermectin 0.1 uk
http://lisinopril.top/# lisinopril 5mg pill
https://stromectol.fun/# cost of ivermectin pill
lasix: Over The Counter Lasix – buy lasix online
online order prednisone prednisone 2.5 mg tab prednisone ordering online
http://amoxil.cheap/# amoxicillin 500mg capsule buy online
https://indianph.com/# indian pharmacy
buy medicines online in india
https://indianph.xyz/# india pharmacy mail order
india pharmacy
http://indianph.xyz/# indian pharmacies safe
best online pharmacy india
https://indianph.xyz/# indian pharmacies safe
best online pharmacy india
https://indianph.com/# indianpharmacy com
top 10 pharmacies in india
http://indianph.com/# top 10 online pharmacy in india
https://indianph.xyz/# indian pharmacy paypal
top online pharmacy india
http://indianph.xyz/# reputable indian pharmacies
Online medicine home delivery
Online medicine home delivery indian pharmacies safe Online medicine home delivery
https://cipro.guru/# ciprofloxacin generic
http://cytotec24.shop/# Cytotec 200mcg price
https://diflucan.pro/# diflucan capsule price
https://nolvadex.guru/# tamoxifen alternatives
http://nolvadex.guru/# alternatives to tamoxifen
http://nolvadex.guru/# raloxifene vs tamoxifen
buy doxycycline cheap doxy 200 price of doxycycline
http://doxycycline.auction/# doxycycline generic
https://doxycycline.auction/# doxycycline 100mg price
diflucan tablet 100 mg diflucan capsule 50 mg diflucan 150 mg
https://doxycycline.auction/# doxycycline 100mg dogs
https://cytotec24.shop/# buy misoprostol over the counter
doxycycline 100 mg doxycycline generic buy doxycycline without prescription
http://cytotec24.shop/# buy cytotec in usa
http://doxycycline.auction/# doxycycline online
buy ciprofloxacin buy cipro ciprofloxacin 500mg buy online
http://cipro.guru/# buy cipro cheap
http://doxycycline.auction/# order doxycycline 100mg without prescription
https://lanarhoades.fun/# lana rhoades filmleri
https://lanarhoades.fun/# lana rhoades izle
https://abelladanger.online/# Abella Danger
http://evaelfie.pro/# eva elfie filmleri
https://sweetiefox.online/# swetie fox
Your blog posts never fail to entertain and educate me. I especially enjoyed the recent one about [insert topic]. Keep up the great work!
http://sweetiefox.online/# Sweetie Fox
https://abelladanger.online/# abella danger video
https://lanarhoades.fun/# lana rhoades filmleri
https://sweetiefox.online/# Sweetie Fox izle
http://lanarhoades.fun/# lana rhoades
http://evaelfie.pro/# eva elfie filmleri
http://abelladanger.online/# abella danger video
lana rhoades: lana rhoades izle – lana rhoades izle
http://angelawhite.pro/# ?????? ????
http://evaelfie.pro/# eva elfie filmleri
https://sweetiefox.online/# sweety fox
Your writing is so eloquent and engaging You have a gift for connecting with your readers and making us feel understood
https://angelawhite.pro/# Angela White
http://abelladanger.online/# Abella Danger
http://evaelfie.pro/# eva elfie izle
https://lanarhoades.fun/# lana rhoades izle
http://evaelfie.pro/# eva elfie izle
http://sweetiefox.online/# Sweetie Fox izle
Sweetie Fox video: Sweetie Fox – Sweetie Fox modeli
http://lanarhoades.fun/# lana rhoades izle
https://angelawhite.pro/# Angela White video
lana rhoades full video: lana rhoades videos – lana rhoades boyfriend
free single dating sites: http://evaelfie.site/# eva elfie full videos
mia malkova latest: mia malkova movie – mia malkova movie
eva elfie videos: eva elfie new video – eva elfie full video
meet single women online: https://lanarhoades.pro/# lana rhoades boyfriend
http://miamalkova.life/# mia malkova photos
lana rhoades: lana rhoades videos – lana rhoades hot
eva elfie hd: eva elfie full videos – eva elfie photo
https://sweetiefox.pro/# sweetie fox
eva elfie new videos: eva elfie new videos – eva elfie full video
asian dating sites: http://lanarhoades.pro/# lana rhoades full video
https://evaelfie.site/# eva elfie hd
mia malkova new video: mia malkova movie – mia malkova latest
eva elfie full video: eva elfie new video – eva elfie hd
sweetie fox full video: sweetie fox video – sweetie fox full
http://evaelfie.site/# eva elfie
victoriasonlinedating: http://miamalkova.life/# mia malkova videos
lana rhoades pics: lana rhoades videos – lana rhoades solo
lana rhoades videos: lana rhoades solo – lana rhoades solo
https://lanarhoades.pro/# lana rhoades boyfriend
eva elfie new videos: eva elfie new video – eva elfie new video
ourtime dating site log in: https://lanarhoades.pro/# lana rhoades full video
http://sweetiefox.pro/# sweetie fox
eva elfie videos: eva elfie – eva elfie full video
As a fellow blogger, I can appreciate the time and effort that goes into creating well-crafted posts You are doing an amazing job
http://miamalkova.life/# mia malkova movie
lana rhoades videos: lana rhoades videos – lana rhoades solo
sweetie fox video: sweetie fox video – sweetie fox
eva elfie photo: eva elfie videos – eva elfie hd
sweetie fox full: sweetie fox full – sweetie fox full
http://sweetiefox.pro/# ph sweetie fox
free dating sites for men: http://miamalkova.life/# mia malkova latest
eva elfie full videos: eva elfie hot – eva elfie new videos
aviator: aviator login – aviator sportybet ghana
aviator sinyal hilesi: aviator – pin up aviator
melhor jogo de aposta: jogos que dão dinheiro – ganhar dinheiro jogando
https://aviatorghana.pro/# aviator betting game
aviator malawi: aviator bet – aviator bet malawi login
ganhar dinheiro jogando: jogos que dao dinheiro – ganhar dinheiro jogando
aviator hilesi: pin up aviator – aviator oyna
aviator betting game: aviator game bet – aviator game online
pin-up casino entrar: cassino pin up – cassino pin up
aviator online: aviator mz – aviator online
http://aviatormalawi.online/# aviator malawi
aviator betting game: aviator malawi – aviator
aviator game online: aviator game bet – aviator game bet
jogo de aposta: melhor jogo de aposta – depósito mínimo 1 real
aviator oyna slot: aviator sinyal hilesi – pin up aviator
aviator bet: aviator bet malawi – aviator game
jogo de aposta online: jogos que dão dinheiro – melhor jogo de aposta para ganhar dinheiro
aviator pin up: aviator betano – aviator jogo
buy cheap zithromax online: hydroxychloroquine zinc and zithromax zithromax online australia
aviator: aviator moçambique – aviator
can i buy zithromax over the counter in canada – https://azithromycin.pro/zithromax-non-prescription.html where can i purchase zithromax online
play aviator: aviator betting game – aviator bet malawi login
zithromax antibiotic without prescription: azithromycin zithromax 500mg price where can i buy zithromax capsules
aviator bahis: aviator oyna slot – aviator oyunu
canadian pharmacy review International Pharmacy delivery northern pharmacy canada canadianpharm.store
canadian pharmacy ed medications: Certified Canadian pharmacies – best canadian pharmacy online canadianpharm.store
п»їbest mexican online pharmacies: mexican pharmacy – mexican rx online mexicanpharm.shop
https://indianpharm24.shop/# mail order pharmacy india indianpharm.store
http://canadianpharmlk.com/# buying drugs from canada canadianpharm.store
http://indianpharm24.com/# india pharmacy indianpharm.store
https://mexicanpharm24.com/# mexican online pharmacies prescription drugs mexicanpharm.shop
http://indianpharm24.com/# world pharmacy india indianpharm.store
http://indianpharm24.com/# top 10 pharmacies in india indianpharm.store
buy prescription drugs from canada cheap: CIPA approved pharmacies – canadian pharmacy king canadianpharm.store
http://indianpharm24.shop/# online pharmacy india indianpharm.store
http://canadianpharmlk.shop/# reliable canadian online pharmacy canadianpharm.store
https://indianpharm24.com/# india online pharmacy indianpharm.store
buying from online mexican pharmacy Medicines Mexico mexico drug stores pharmacies mexicanpharm.shop
http://mexicanpharm24.shop/# medicine in mexico pharmacies mexicanpharm.shop
https://indianpharm24.shop/# indian pharmacy online indianpharm.store
mexico pharmacies prescription drugs: Mexico pharmacy price list – reputable mexican pharmacies online mexicanpharm.shop
https://canadianpharmlk.com/# best canadian pharmacy canadianpharm.store
http://canadianpharmlk.shop/# online canadian drugstore canadianpharm.store
Consider the values embedded in technology and innovation. How do societal values influence the development and use of technology?
http://canadianpharmlk.shop/# canadian pharmacy world canadianpharm.store
medicine in mexico pharmacies mexican online pharmacies prescription drugs п»їbest mexican online pharmacies mexicanpharm.shop
http://indianpharm24.com/# indian pharmacy online indianpharm.store
https://mexicanpharm24.shop/# best online pharmacies in mexico mexicanpharm.shop
prednisone cost us how can i get prednisone online without a prescription prednisone brand name canada
cost of generic clomid no prescription: how long does it take for clomid to work in males – cost cheap clomid pills
buy prednisone online no prescription: where to buy prednisone without prescription – prednisone cost us
https://clomidst.pro/# get clomid now
medicine prednisone 10mg: cheap generic prednisone – india buy prednisone online
http://amoxilst.pro/# amoxacillian without a percription
how to get amoxicillin: amoxicillin for pneumonia – amoxicillin 775 mg
can i get generic clomid prices can i get generic clomid price where can i buy cheap clomid without insurance
https://amoxilst.pro/# where can you get amoxicillin
where can i buy cheap clomid without prescription: where to buy cheap clomid tablets – cost generic clomid without a prescription
can you buy cheap clomid no prescription: can i order generic clomid tablets – where to get clomid
buy cheap prednisone: prednisone long term side effects – prednisone 15 mg tablet
http://prednisonest.pro/# prednisone over the counter uk
prednisone 5mg daily: order prednisone from canada – prednisone 54
http://prednisonest.pro/# cheap generic prednisone
can i get generic clomid without dr prescription buy cheap clomid no prescription where to get generic clomid price
amoxicillin 1000 mg capsule: amoxicillin 500mg capsules – buy amoxicillin from canada
5 mg prednisone tablets: prednisone taper schedule – best pharmacy prednisone
http://clomidst.pro/# order generic clomid without insurance
prednisone no rx: when do prednisone side effects start – price for 15 prednisone
buy prescription online: no prescription drugs online – online medication no prescription
erectile dysfunction medications online: buy ed medication online – buy ed pills online
http://edpills.guru/# ed online pharmacy
canada drugs coupon code: canada online pharmacy – online pharmacy no prescription
https://edpills.guru/# affordable ed medication
canadian pharmacy world coupons: canada pharmacy online – canadian pharmacy without prescription
best no prescription online pharmacy: online drugstore no prescription – buy drugs online without prescription
reputable online pharmacy no prescription: Online pharmacy USA – buying prescription drugs from canada
https://edpills.guru/# cheap ed pills
п»їed pills online pills for erectile dysfunction online affordable ed medication
canadian pharmacy without a prescription: no prescription needed online pharmacy – canadian pharmacy online no prescription needed
canadian pharmacy discount code: mexican online pharmacy – cheapest pharmacy prescription drugs
https://pharmnoprescription.pro/# cheap prescription drugs online
online ed pills: cost of ed meds – discount ed meds
http://edpills.guru/# best ed pills online
no prescription pharmacy online: canada drugs no prescription – online pharmacy no prescriptions
erection pills online: cheap ed – order ed pills online
canadian drugs no prescription mexico online pharmacy prescription drugs no prescription canadian pharmacies
https://mexicanpharm.online/# mexican rx online
https://canadianpharm.guru/# canadian pharmacy drugs online
mexican drugstore online medication from mexico pharmacy pharmacies in mexico that ship to usa
canadian valley pharmacy: canadian pharmacy in canada – legit canadian online pharmacy
buy prescription online: online meds no prescription – online pharmacy no prescription needed
https://pharmacynoprescription.pro/# indian pharmacy no prescription
pharmacy online no prescription: can i buy prescription drugs in canada – quality prescription drugs canada
https://pharmacynoprescription.pro/# buy drugs without prescription
canadian pharmacy no scripts: canadian drugs online – is canadian pharmacy legit
http://pharmacynoprescription.pro/# best online pharmacies without prescription
best non prescription online pharmacy online pharmacy without prescriptions meds online no prescription
reputable indian online pharmacy: indian pharmacy online – best india pharmacy
http://mexicanpharm.online/# purple pharmacy mexico price list
canadian pharmacy sarasota: buy prescription drugs from canada cheap – canadian pharmacies compare
http://mexicanpharm.online/# mexican online pharmacies prescription drugs
real canadian pharmacy: canadian discount pharmacy – canadian discount pharmacy
canada drugs online review: precription drugs from canada – canadian neighbor pharmacy
https://pharmacynoprescription.pro/# pills no prescription
indian pharmacies safe: indianpharmacy com – top 10 pharmacies in india
http://canadianpharm.guru/# 77 canadian pharmacy
buying prescription drugs in mexico buying prescription drugs in mexico online mexico drug stores pharmacies
buying prescription drugs in mexico: best mexican online pharmacies – medicine in mexico pharmacies
http://indianpharm.shop/# world pharmacy india
buying prescription drugs in mexico: mexican rx online – buying prescription drugs in mexico online
reputable indian pharmacies: india pharmacy – india pharmacy
https://pharmacynoprescription.pro/# quality prescription drugs canada
canadianpharmacymeds com: canadian pharmacies comparison – canadian drug stores
mexican online pharmacies prescription drugs: medication from mexico pharmacy – buying prescription drugs in mexico online
http://pharmacynoprescription.pro/# no prescription pharmacy online
indian pharmacy paypal buy medicines online in india pharmacy website india
canadian prescriptions in usa: best non prescription online pharmacy – no prescription canadian pharmacies
http://pharmacynoprescription.pro/# no prescription pharmacy
mexican pharmaceuticals online: mexican rx online – mexico drug stores pharmacies
reputable mexican pharmacies online: best mexican online pharmacies – reputable mexican pharmacies online
https://mexicanpharm.online/# mexican rx online
mexican drugstore online: best online pharmacies in mexico – mexican online pharmacies prescription drugs
indian pharmacies safe india pharmacy mail order indian pharmacy paypal
canadian drugstore online: buy canadian drugs – buying drugs from canada
https://indianpharm.shop/# п»їlegitimate online pharmacies india
canadian and international prescription service: purchasing prescription drugs online – best no prescription online pharmacies
http://pharmacynoprescription.pro/# buying prescription drugs in canada
indian pharmacy online: buy prescription drugs from india – india pharmacy mail order
mexican mail order pharmacies: buying from online mexican pharmacy – purple pharmacy mexico price list
https://indianpharm.shop/# best india pharmacy
sweet bonanza oyna: sweet bonanza bahis – guncel sweet bonanza
http://aviatoroyna.bid/# aviator sinyal hilesi ücretsiz
sweet bonanza yasal site: sweet bonanza guncel – sweet bonanza
http://sweetbonanza.bid/# sweet bonanza yorumlar
https://slotsiteleri.guru/# bonus veren slot siteleri
sweet bonanza indir: sweet bonanza kazanma saatleri – sweet bonanza slot demo
https://pinupgiris.fun/# pin-up giris
pin up giris: pin-up casino – pin up guncel giris
http://aviatoroyna.bid/# aviator uçak oyunu
aviator casino oyunu: aviator ucak oyunu – aviator
https://gatesofolympus.auction/# gates of olympus demo türkçe
pin up: pin-up online – pin up casino giris
http://aviatoroyna.bid/# aviator hilesi ucretsiz
http://pinupgiris.fun/# pin up 7/24 giris
gates of olympus giris: gates of olympus demo – gates of olympus oyna ucretsiz
https://aviatoroyna.bid/# aviator uçak oyunu
aviator oyna: aviator sinyal hilesi – aviator hile
http://slotsiteleri.guru/# slot casino siteleri
http://sweetbonanza.bid/# sweet bonanza mostbet
https://pinupgiris.fun/# pin-up giris
slot siteleri bonus veren: bonus veren casino slot siteleri – bonus veren slot siteleri
https://slotsiteleri.guru/# deneme veren slot siteleri
https://sweetbonanza.bid/# sweet bonanza güncel
guncel sweet bonanza: sweet bonanza nas?l oynan?r – sweet bonanza oyna
pin-up casino indir: pin-up giris – pin-up online
https://slotsiteleri.guru/# canli slot siteleri
gates of olympus 1000 demo: gates of olympus demo oyna – gates of olympus 1000 demo
https://aviatoroyna.bid/# aviator oyunu giris
http://aviatoroyna.bid/# aviator nasil oynanir
aviator bahis: aviator sinyal hilesi ucretsiz – aviator oyunu 50 tl
pin up indir: pin up casino giris – pin up casino
https://aviatoroyna.bid/# aviator oyunu 10 tl
https://indianpharmacy.icu/# best online pharmacy india
mexican border pharmacies shipping to usa reputable mexican pharmacies online mexican mail order pharmacies
http://indianpharmacy.icu/# indianpharmacy com
canadian drugs pharmacy: my canadian pharmacy rx – canada cloud pharmacy
online pharmacy india: indian pharmacy – india online pharmacy
best online canadian pharmacy: Licensed Canadian Pharmacy – online pharmacy canada
canada drug pharmacy: Licensed Canadian Pharmacy – is canadian pharmacy legit
legitimate canadian mail order pharmacy: canadian pharmacy 24 – canadian pharmacy 24
mexican pharmacy mexico pharmacy mexican pharmacy
legal to buy prescription drugs from canada: Certified Canadian Pharmacy – canadianpharmacymeds
https://canadianpharmacy24.store/# canadian online pharmacy
best online pharmacies in mexico: mexico pharmacy – mexican rx online
reputable mexican pharmacies online: mexico pharmacy – mexican rx online
mexican pharmaceuticals online Mexican Pharmacy Online medication from mexico pharmacy
best mexican online pharmacies: Online Pharmacies in Mexico – pharmacies in mexico that ship to usa
online pharmacy india: Cheapest online pharmacy – legitimate online pharmacies india
top online pharmacy india: indian pharmacy delivery – top 10 online pharmacy in india
online shopping pharmacy india: indian pharmacy delivery – indian pharmacies safe
http://indianpharmacy.icu/# reputable indian pharmacies
canada rx pharmacy: Prescription Drugs from Canada – reputable canadian pharmacy
legitimate canadian pharmacy Certified Canadian Pharmacy best canadian online pharmacy
indian pharmacies safe: india pharmacy mail order – indian pharmacy online
where to buy generic clomid without a prescription buying clomid without prescription can i order generic clomid without dr prescription
https://amoxilall.shop/# amoxicillin 500mg capsules
prednisone 50 mg tablet cost over the counter prednisone pills cost of prednisone tablets
https://zithromaxall.shop/# buy zithromax online australia
zithromax purchase online: zithromax 500mg – zithromax azithromycin
http://clomidall.com/# can i order generic clomid pills
50 mg prednisone from canada: cost of prednisone – prednisone for dogs
https://zithromaxall.com/# zithromax 500mg over the counter
https://prednisoneall.shop/# prednisone online for sale
https://zithromaxall.shop/# where to buy zithromax in canada
http://zithromaxall.com/# cost of generic zithromax
zithromax prescription in canada: zithromax – zithromax 500 mg for sale
https://amoxilall.shop/# amoxicillin 250 mg price in india
Kamagra 100mg price: Sildenafil Oral Jelly – buy Kamagra
Sildenafil Citrate Tablets 100mg: best price on viagra – Viagra generic over the counter
sildenafil 50 mg price: cheapest viagra – Order Viagra 50 mg online
Cheap Sildenafil 100mg buy viagra online Cheap generic Viagra online
Cheap generic Viagra online: best price on viagra – Cheap Viagra 100mg
buy kamagra online usa: Kamagra Iq – cheap kamagra
http://kamagraiq.com/# Kamagra 100mg price
Kamagra Oral Jelly: kamagra best price – buy Kamagra
viagra without prescription: generic ed pills – viagra canada
cheapest viagra: viagra without prescription – cheapest viagra
https://kamagraiq.shop/# sildenafil oral jelly 100mg kamagra
Viagra Tablet price: best price on viagra – Viagra online price
buy Kamagra: Sildenafil Oral Jelly – super kamagra
http://sildenafiliq.com/# Viagra Tablet price
http://tadalafiliq.com/# Buy Cialis online
Kamagra 100mg price: cheap kamagra – buy Kamagra
https://kamagraiq.shop/# Kamagra 100mg price
buy Viagra over the counter: Order Viagra 50 mg online – sildenafil online
Buy Tadalafil 20mg: Generic Tadalafil 20mg price – Tadalafil Tablet
http://kamagraiq.com/# super kamagra
cialis generic: cialis best price – Tadalafil Tablet
buy Kamagra: Sildenafil Oral Jelly – Kamagra 100mg price
http://sildenafiliq.com/# generic sildenafil
Cheap generic Viagra online: best price on viagra – Cheap Sildenafil 100mg
https://kamagraiq.shop/# п»їkamagra
Tadalafil Tablet: Buy Tadalafil 5mg – cheapest cialis
https://sildenafiliq.com/# sildenafil 50 mg price
buy kamagra online usa: kamagra best price – cheap kamagra
super kamagra Kamagra Oral Jelly Price sildenafil oral jelly 100mg kamagra
https://kamagraiq.com/# super kamagra
Viagra tablet online: sildenafil iq – buy Viagra online
https://indianpharmgrx.shop/# buy medicines online in india
http://canadianpharmgrx.xyz/# canadian pharmacies compare
https://indianpharmgrx.com/# Online medicine home delivery
http://mexicanpharmgrx.shop/# purple pharmacy mexico price list
mexican rx online: online pharmacy in Mexico – mexican pharmaceuticals online
canadian pharmacy world canadian pharmacy canadianpharmacy com
https://mexicanpharmgrx.com/# buying from online mexican pharmacy
buying prescription drugs in mexico online: mexican drugstore online – buying from online mexican pharmacy
https://mexicanpharmgrx.shop/# mexican border pharmacies shipping to usa
http://canadianpharmgrx.com/# canadian pharmacy 24 com
https://indianpharmgrx.shop/# top 10 pharmacies in india
https://mexicanpharmgrx.shop/# mexico drug stores pharmacies
mexico pharmacies prescription drugs: reputable mexican pharmacies online – medicine in mexico pharmacies
https://mexicanpharmgrx.shop/# reputable mexican pharmacies online
http://mexicanpharmgrx.com/# buying prescription drugs in mexico
http://mexicanpharmgrx.shop/# mexican pharmaceuticals online
http://mexicanpharmgrx.shop/# medication from mexico pharmacy
doxycycline 100mg online: generic doxycycline – buy doxycycline for dogs
http://misoprostol.top/# Abortion pills online
doxycycline 100mg: buy cheap doxycycline – doxylin
Abortion pills online: buy misoprostol over the counter – buy cytotec pills online cheap
doxycycline monohydrate: doxycycline without prescription – doxycycline hyclate
buy cytotec pills online cheap: order cytotec online – purchase cytotec
buy cytotec pills: cytotec abortion pill – buy cytotec pills online cheap
http://misoprostol.top/# cytotec pills buy online
doxycycline 500mg: purchase doxycycline online – online doxycycline
buy cipro antibiotics cipro buy generic ciprofloxacin
Abortion pills online: cytotec pills online – buy cytotec over the counter
order doxycycline: doxycycline 100mg capsules – buy doxycycline online 270 tabs
doxycycline: generic for doxycycline – generic doxycycline
http://misoprostol.top/# buy cytotec
diflucan online nz: diflucan pill over the counter – where to purchase over the counter diflucan pill
doxycycline: buy doxycycline – where to get doxycycline
purchase cipro: ciprofloxacin 500 mg tablet price – ciprofloxacin order online
diflucan capsules 100mg: can i buy diflucan in mexico – diflucan online cheap without a prescription
https://misoprostol.top/# buy cytotec
ciprofloxacin generic price: buy generic ciprofloxacin – buy cipro online canada
tamoxifen blood clots: does tamoxifen cause joint pain – tamoxifen skin changes
buy cytotec: purchase cytotec – Misoprostol 200 mg buy online
ciprofloxacin cipro pharmacy cipro pharmacy
buy cheap amoxicillin online: amoxicillin 500 tablet – amoxicillin for sale
can you buy generic clomid online: where can i get cheap clomid for sale – buying cheap clomid
prednisone price: prednisone buy canada – prednisone 2.5 mg cost
prednisone in canada: buy prednisone online uk – 50 mg prednisone from canada
generic clomid tablets: cost of cheap clomid tablets – can i buy generic clomid no prescription
https://amoxicillina.top/# buy amoxicillin online uk
http://amoxicillina.top/# where to buy amoxicillin pharmacy
average cost of prednisone 20 mg 20mg prednisone prednisone steroids
order amoxicillin no prescription: where can you buy amoxicillin over the counter – buy amoxicillin 500mg uk
http://azithromycina.pro/# can i buy zithromax online
amoxicillin 500mg tablets price in india: amoxicillin without a prescription – amoxicillin over the counter in canada
can i get generic clomid without insurance: can i buy cheap clomid tablets – can you get generic clomid without insurance
medications online without prescriptions: canadian pharmacy no prescription needed – quality prescription drugs canada
http://medicationnoprescription.pro/# buy drugs online without a prescription
online pharmacy no prescription offshore pharmacy no prescription canadian pharmacy no prescription needed
https://medicationnoprescription.pro/# no prescription medicine
get ed prescription online erection pills online online erectile dysfunction
order ed pills: how to get ed pills – affordable ed medication
https://onlinepharmacyworld.shop/# cheapest pharmacy for prescriptions without insurance
http://onlinepharmacyworld.shop/# online pharmacy discount code
http://edpill.top/# online ed medicine
no prescription canadian pharmacy: meds online without prescription – best online pharmacy that does not require a prescription in india
https://onlinepharmacyworld.shop/# prescription free canadian pharmacy
ed treatments online: buy ed pills online – ed treatment online
cheap ed pills online buy erectile dysfunction pills cheap ed
https://medicationnoprescription.pro/# no prescription needed pharmacy
https://medicationnoprescription.pro/# meds online no prescription
online ed drugs: buying ed pills online – ed pills
buying ed pills online online ed drugs ed pills
casino tr?c tuy?n vi?t nam: casino tr?c tuy?n uy tín – game c? b?c online uy tín
web c? b?c online uy tin casino tr?c tuy?n vi?t nam casino tr?c tuy?n vi?t nam
https://casinvietnam.com/# choi casino tr?c tuy?n tren di?n tho?i
casino tr?c tuy?n uy tín: casino tr?c tuy?n vi?t nam – casino tr?c tuy?n vi?t nam
game c? b?c online uy tin casino tr?c tuy?n casino tr?c tuy?n vi?t nam
https://casinvietnam.com/# casino tr?c tuy?n vi?t nam
http://casinvietnam.com/# danh bai tr?c tuy?n
http://mexicoph24.life/# pharmacies in mexico that ship to usa
https://canadaph24.pro/# prescription drugs canada buy online
https://canadaph24.pro/# canadian pharmacy online
http://mexicoph24.life/# mexico pharmacy
https://indiaph24.store/# buy medicines online in india
https://canadaph24.pro/# best canadian online pharmacy
http://canadaph24.pro/# reddit canadian pharmacy
http://indiaph24.store/# india pharmacy
http://canadaph24.pro/# best canadian online pharmacy
http://canadaph24.pro/# canadian pharmacy meds
http://indiaph24.store/# indian pharmacy online
https://canadaph24.pro/# trusted canadian pharmacy
https://canadaph24.pro/# adderall canadian pharmacy
https://mexicoph24.life/# mexico pharmacy
reputable indian online pharmacy indian pharmacy indian pharmacy
http://mexicoph24.life/# mexican pharmacy
http://canadaph24.pro/# canadian mail order pharmacy
recommended canadian pharmacies Licensed Canadian Pharmacy recommended canadian pharmacies
http://indiaph24.store/# indian pharmacy
https://canadaph24.pro/# prescription drugs canada buy online
http://indiaph24.store/# indian pharmacies safe
https://indiaph24.store/# indian pharmacy paypal
legitimate canadian pharmacies Prescription Drugs from Canada canadian valley pharmacy
reputable mexican pharmacies online mexico pharmacy mexican mail order pharmacies
https://indiaph24.store/# indian pharmacy paypal
buy ciprofloxacin over the counter: cipro 500mg best prices – buy cipro online
https://ciprofloxacin.tech/# buy cipro